Veris blogs
In a world obsessed with cybersecurity, firewalls, and encrypted data, it's easy to forget the most basic threat vector: the front door.
While organizations pour millions into digital protection, physical access remains a critical vulnerability. Who walks into your buildings, labs, or server rooms matters just as much—if not more—than who logs into your network.
A physical access control system (PACS) is a security framework that governs who can enter which physical spaces, and when, ensuring only authorized individuals gain access while everyone else stays out.
More than just locked doors or keycards, PACS is a strategic fusion of hardware, software, and human oversight. It uses sensors, credentials, smart readers, and centralized intelligence to safeguard your real-world assets—from corporate campuses to high-security labs.
Because in current scenario, protecting your people, property, and data starts at the threshold.
What is a physical access control system (PACS)?
A physical access control system (PACS) is a modern security solution designed to manage, monitor, and restrict access to physical locations, from entire buildings to specific rooms or restricted zones. At its core, PACS ensures that only authorized individuals—employees, visitors, or contractors—can enter designated areas, and only at approved times. This fine-tuned control helps prevent breaches, protect sensitive assets, and maintain operational safety.
Unlike traditional locks and keys or manual security checks, a PACS is automated, intelligent, and scalable. It verifies identities using credentials (like keycards, biometrics, or mobile devices), processes them through access rules, and makes real-time decisions—all without the delays or blind spots of human-only systems.
This shift from analog to automated access isn't just a tech upgrade, it is a fundamental transformation in how organizations safeguard the physical side of security.
Key components of a physical access control system
A well-functioning physical access control system (PACS) is built on a network of integrated components, each playing a crucial role in keeping unauthorized individuals out, and authorized ones flowing securely through.
- Access points: These are the physical gateways, doors, turnstiles, gates, or elevators—that the system controls. Each access point becomes a checkpoint where entry is either granted or denied based on credentials.
- Credentials: These are the tools users present to identify themselves:
- Keycards or fobs for swipe or tap access.
- PIN codes entered on a keypad.
- Biometric data like fingerprints or facial scans.
- Smartphones using NFC, Bluetooth, or QR-based mobile credentials Each credential ties back to a specific user profile within the system.
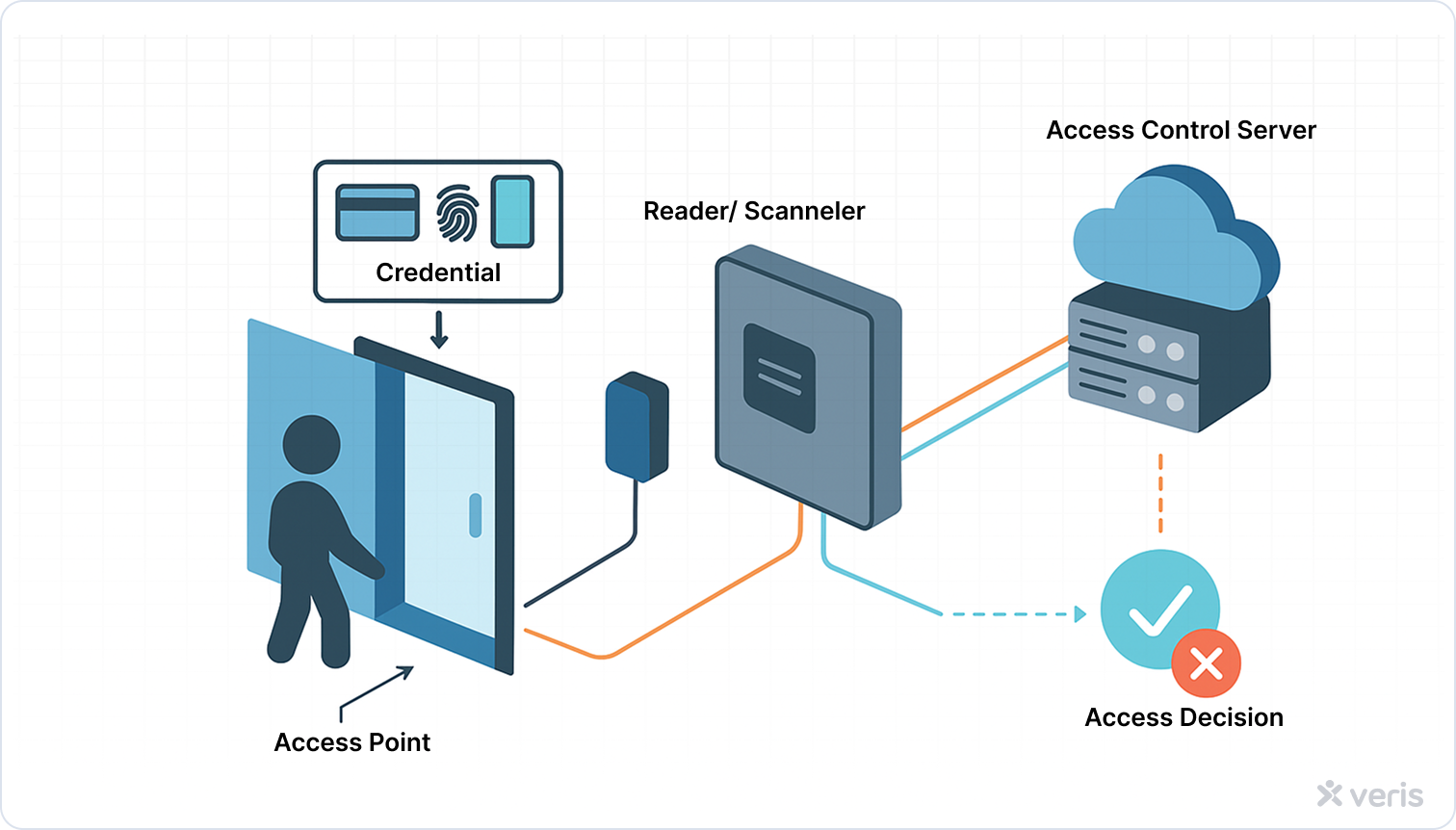
- Readers/scanners: Installed at access points, these devices read the credentials presented by a user and send that data to the control panel for verification. Whether it’s a badge reader, biometric scanner, or mobile QR reader, this is the system’s first contact point.
- Controllers: Often referred to as the “brain” of the system, the controller receives data from the reader, checks authorization rules, and makes the real-time decision to unlock (or deny) the access point. It acts instantly, and logs the event.
- Access control server: This is the central intelligence hub, whether hosted on-premise or in the cloud. It:
- Stores user profiles and access rules
- Manages system configurations
- Logs every access attempt
- Enables remote control and analytics
Modern PACS often favor cloud servers for scalability, multi-site control, and real-time management.
How a physical access control system works ?
A physical access control system operates through a streamlined sequence of actions, each step working behind the scenes to ensure secure, efficient access. Here’s how it all comes together:
1. Authorization: The process begins with administrators assigning access permissions. Each user—whether an employee, contractor, or visitor, is granted customized access based on:
- Who they are
- Where they need to go
- When they’re allowed to enter
Permissions can be as broad or as specific as needed, from 24/7 building-wide access to time-limited entry into one room.
2. Authentication: At the access point (like a door or gate), the user presents their credential—a badge, PIN, fingerprint, or mobile app.
The system verifies that credential against stored data to confirm who the person is.
3. Access decision: Based on the rules defined during authorization, the system immediately decides:
- Grant access and unlock the door
- Deny access and trigger an alert or log the attempt
This decision is made in milliseconds by the system’s controller—removing human error from the equation.
4. Monitoring & logging: Every access attempt successful or not, is recorded. These logs provide:
- An audit trail for investigations or reviews
- Compliance reports for regulated environments
- Real-time alerts for unusual or suspicious activity
5. System integration: Modern PACS can be integrated with other workplace or security systems, including:
- Video surveillance (CCTV)
- Alarm and intrusion detection systems
- Visitor management platforms
- Emergency response protocols
This creates a unified security ecosystem, enhancing visibility, control, and response speed.
When all five steps are working in sync, you get more than just a locked door, you get a dynamic, intelligent access control experience that scales with your security needs.
Common credentials and authentication methods in PACS
PACS can accommodate a wide range of credentials to suit different levels of security, user convenience, and operational needs. Below is a breakdown of the most common authentication methods:
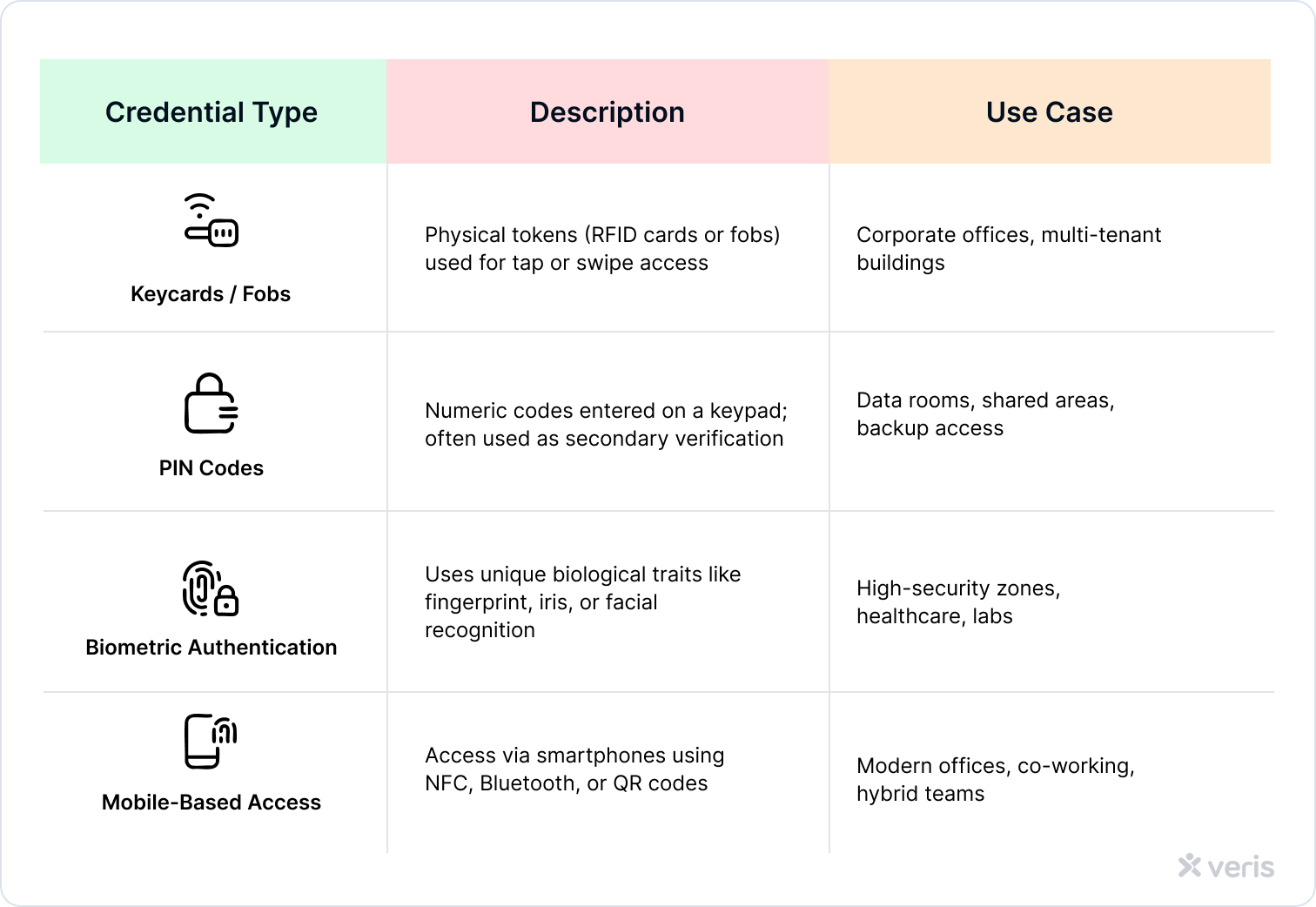
PACS can accommodate a wide range of credentials to suit different levels of security, user convenience, and operational needs. Below is a breakdown of the most common authentication methods:
Why do physical access control systems matter?
Physical access control systems are not just about keeping doors locked—they’re about creating controlled, responsive, and transparent environments where security meets scalability.
Here’s why PACS plays a vital role in safeguarding today’s workplaces:
- Improved security at sensitive touch points: Whether it’s a data center, executive suite, or R&D lab, PACS ensures that only the right people have access, reducing the risk of unauthorized entry, theft, or sabotage.
- User-level control over access rights: PACS allows for granular permission settings, letting administrators define exactly who can go where, and when. Access can be customized by role, department, time of day, or even specific events.
- Full audit trails for compliance: Every access attempt is logged—successes, denials, and anomalies—creating a detailed, time-stamped audit trail that supports internal investigations, regulatory compliance, and operational transparency.
- Remote management through cloud-based systems: Modern PACS platforms allow remote access control, credential updates, and real-time monitoring via web dashboards—ideal for managing multi-site operations or hybrid workforces.
- Integrated ecosystem with other security technologies: PACS can be synced with:
- Video surveillance (CCTV)
- Intrusion detection systems
- Emergency response protocols
- Visitor management tools
This turns your physical access control into a central node of a unified, intelligent security infrastructure. In short, PACS is no longer a nice-to-have, it is a non-negotiable layer of modern security, woven into every door, checkpoint, and access event in your physical environment.
Physical access control systems: Real-world use cases
Physical access control systems are not just security add-ons, they are mission-critical infrastructure across industries where control, compliance, and safety are non-negotiable.
Here’s where PACS is making a real-world impact:
- Corporate offices and headquarters: From managing employee access to executive suites, meeting rooms, or server closets, PACS helps enterprises balance security with flexibility—especially in hybrid work environments.
- Hospitals and clinical zones: Healthcare facilities use PACS to restrict access to ICUs, pharmacies, labs, and patient records. This ensures compliance with health regulations and protects both staff and patients from unauthorized access.
- Government and defense facilities: National security sites require airtight access controls. PACS enables multi-factor authentication, biometric verification, and detailed audit logs—ensuring only vetted personnel can access sensitive zones.
- Data centers and server rooms: For businesses handling large volumes of sensitive data, PACS is essential to secure physical hardware. It also provides traceable logs for compliance with data protection standards like GDPR or HIPAA.
- Hotels, co-living spaces, and gyms: These high-traffic, multi-user environments rely on PACS to manage temporary credentials, guest access, and zone-based permissions—offering convenience without compromising safety.
Frequently asked questions(FAQs)
Conclusion: The gatekeeper of the modern workplace security
In a world where security threats are evolving as fast as technology itself, physical access control systems (PACS) have become a foundational layer of protection, not just for doors and gates, but for data, assets, and people.
By blending physical infrastructure with digital intelligence, PACS empowers organizations to go beyond keys and locks. It provides granular control, real-time monitoring, and seamless integration with broader security systems—all while delivering the scalability and convenience modern workplaces demand.
Whether you’re managing a corporate HQ, a hospital, or a residential complex, the message is clear: it’s time to rethink how access is controlled.
Is your current system secure, scalable, and smart enough?
Now is the time to evaluate your existing access controls and consider upgrading to a modern PACS solution that puts both security and usability at the center.
Because in today’s world, the door isn’t just an entry point—it’s your first line of defense.

Jul 17, 2025
Read time: Loading...
What is a physical access control system and why is it important?
Learn how physical access control systems protect your spaces, assets, and people by combining smart tech with scalable, real-time security.
Jul 16, 2025
123
How much of your office space goes unused every single day?
If your answer is anything less than precise, you're not alone—and you're likely leaving money on the table.
As hybrid work becomes the norm and businesses tighten belts in the face of rising real estate costs, the workplace has entered a new era—one that values agility over excess, and efficiency over tradition. Desks sit empty on Fridays, meeting rooms are booked but unused, and facilities teams scramble to make sense of scattered data across spreadsheets, floor plans, and outdated tools.
Enter space management software—the invisible operator behind today’s smartest workplaces. It’s not just about floor plans and seat counts. It’s about reimagining how we use space as a living, dynamic asset—tracked in real time, optimized continuously, and tailored to how your people work. From Fortune 500 campuses to scrappy startups, this tech is quietly transforming the way we think about work environments, making every square foot count.
What is space management software?
Space management software is a digital platform designed to help organizations strategically plan, monitor, and optimize how their physical spaces are used. Whether it’s a bustling office floor, a university campus, or a retail environment, this tool brings visibility, order, and intelligence to every square foot.
At its core, the software manages:
- Physical spaces — from desks and meeting rooms to entire buildings or campuses.
- Occupancy levels — who is using what, when, and how often.
- Resources and assets — furniture, equipment, and shared utilities.
- Booking systems — for rooms, hot desks, or collaboration zones.
It’s tailor-made for today’s dynamic, multi-use environments: hybrid offices, educational institutions, coworking hubs, healthcare facilities, and large enterprises juggling multiple locations.
Unlike traditional tools—think spreadsheets, paper maps, or siloed legacy systems—space management software offers real-time data, interactive floor plans, and automation. That means no more guesswork, no more double-booked rooms, and no more flying blind on occupancy rates. Instead, you're equipped with a single source of truth that evolves with your workplace.
Core functions of space management software
Space management software is not just a digital map of your office—it’s a central command center for how space is used, optimized, and experienced. Here’s what it powers behind the scenes:
- Centralized space data & inventory tracking: Say goodbye to scattered spreadsheets. This software consolidates all your space-related data—available rooms, assigned desks, shared assets, occupancy levels—into one unified dashboard. It’s your single source of truth for smarter decisions.
- Interactive floor plans & space visualization: Visualize your workplace like never before. With interactive floor plans and, in some cases, 3D views, you can see how space is allocated, where teams sit, and what’s underutilized—all in real time. Strategic space planning becomes as easy as drag-and-drop.
- Desk and meeting room booking systems: Enable employees to book spaces with a tap. Whether it’s a hot desk, quiet pod, or huddle room, the system allows seamless self-service reservations synced with your calendar tools. No double bookings. No wasted space. Just frictionless access.
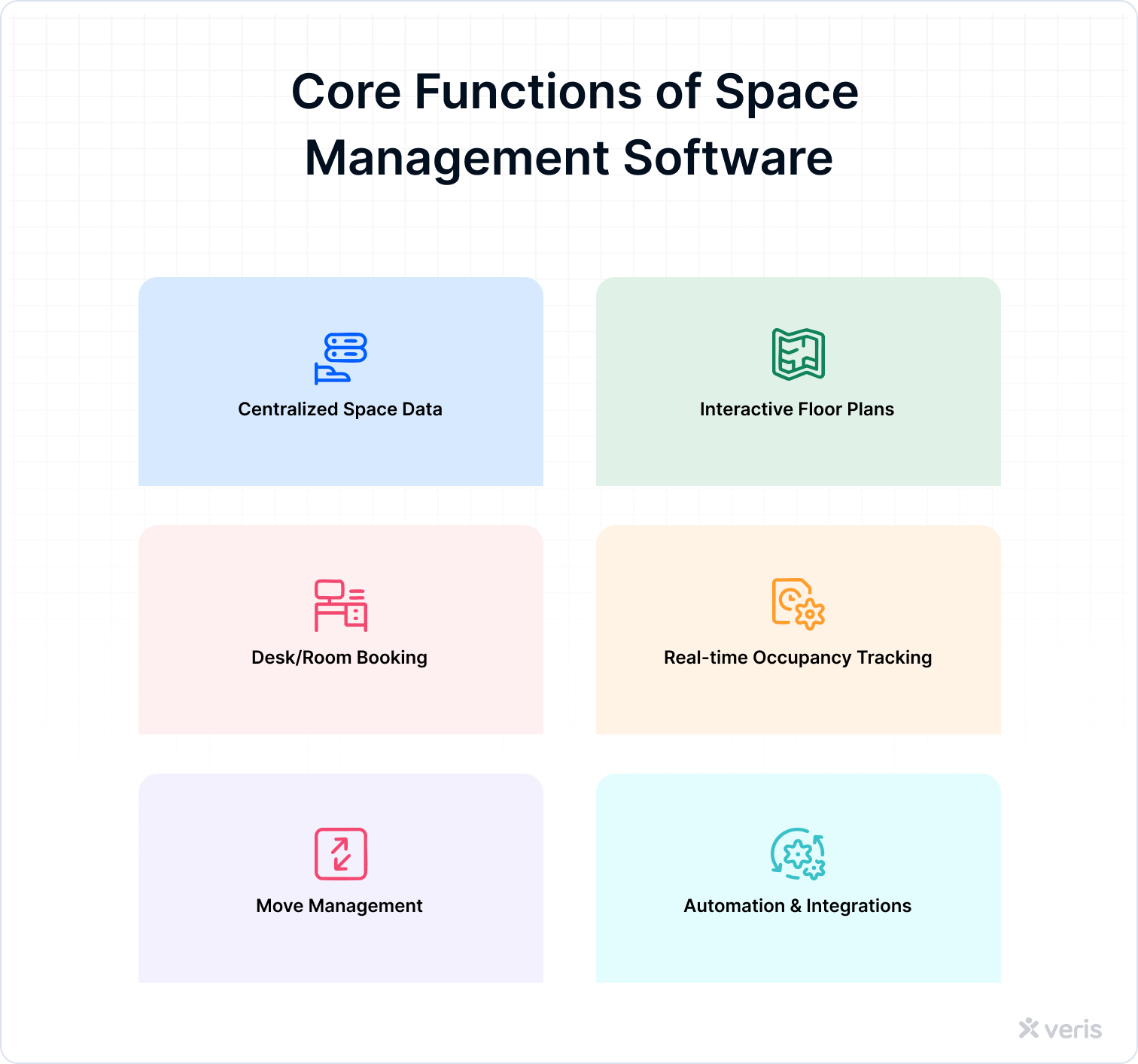
- Real-time occupancy tracking and analytics: Through sensors, badges, or app check-ins, the software captures live usage data—how often rooms are used, which areas are crowded or vacant, and when peak hours hit. With this intel, you can spot patterns, rightsize your space, and plan proactively.
- Move management: Teams, people, and assets: Relocating a team? Shuffling departments? Onboarding new hires? Space management software makes it effortless to reassign desks, move equipment, or redesign entire zones—without the logistical chaos.
- Automation and integrations: Modern platforms integrate with your IoT devices, calendar apps, HR systems, and even building management tools. The result? A fully connected workplace that automates bookings, updates layouts in real time, and keeps everyone in sync—without the manual hustle.
Must have features in a space management software
The best space management tools don’t just show you space—they unlock its full potential. Here are the essential features every modern platform should offer, and why they matter:
Key benefits of using space management software
Beyond floor plans and booking buttons, space management software delivers strategic, measurable impact. Here’s how it pays off—both in real estate and ROI:
- Optimize space utilization: Identify which areas are thriving and which are just collecting dust. Reallocate, repurpose, or retire unused space to get the most out of every square foot.
- Cost savings: Shrink your office footprint, consolidate underused locations, and eliminate inefficiencies in maintenance and operations. Less waste, more value.
- Improve employee experience: Give your people control. With intuitive booking tools and clearer access to the right spaces at the right time, workplace friction drops—and satisfaction rises.
- Scenario planning for growth: Model future space needs, headcount changes, or layout redesigns with data-backed simulations. No guesswork—just strategic foresight.
- Streamline operations: Automate the admin. From booking approvals to occupancy reporting, reduce the manual load so facilities teams can focus on what matters.
- Hybrid-Ready Infrastructure: Support today’s most flexible workstyles. Whether half the team is remote or everyone’s in on Tuesday, your workplace stays organized and optimized.
Space management software: Use cases across industries
Space management software isn not one-size-fits-all—it is a versatile solution powering smarter, more agile environments across sectors. Here’s who’s using it, and why:
- Large enterprises: With sprawling office portfolios and global teams, large organizations rely on space management tools to track occupancy, standardize layouts, and cut down on underused real estate—from HQs to regional hubs.
- Universities and educational campuses: Scheduling classrooms, labs, auditoriums, and event spaces across semesters and departments? These platforms bring order to the chaos—maximizing space and minimizing conflicts across sprawling academic grounds.
- Coworking and flex-space providers: In a world of hot desks and drop-in clients, real-time booking and occupancy visibility are non-negotiable. Space software ensures smooth operations, fair usage, and better customer experience.
- Retail and showrooms: Retailers use it to optimize floor layouts, product displays, and backroom storage. In high-rent locations, every inch matters—and visibility into space usage is key to profitability.
- Healthcare and manufacturing: For facilities with strict compliance needs and high-precision layouts, space management software helps track usage, meet regulatory standards, and ensure smooth movement of people, equipment, and processes.
Frequently ssked questions (FAQs)
Conclusion: Future-proofing the modern workspace
Space is no longer just square footage—it is a strategic asset. And space management software is the engine that ensures every inch is working as hard as your people do.
By delivering real-time visibility, smarter resource allocation, and seamless workplace experiences, this technology transforms how organizations operate—cutting costs, boosting productivity, and enabling agility in a hybrid-first world.
In an era where flexibility is currency and real estate is under the microscope, space management software isn’t a nice-to-have. It’s the blueprint for future-ready workplaces.
Now’s the time to ask: Are you using your space, or is it using you?
Take the first step—audit your space usage and uncover the hidden value in your workplace.
What is space management software: Everything you need to know
Jul 4, 2025
123
In today’s ever-evolving world of work, one term continues to dominate boardroom conversations and HR strategy decks: hybrid work schedule.
Born out of necessity during the COVID-19 pandemic and refined through ongoing experimentation, the hybrid model has become the blueprint for how modern organizations operate. As businesses reopened physical offices, the one-size-fits-all approach to work—commuting five days a week—no longer made sense. Employees wanted flexibility. Employers wanted productivity and culture. The hybrid schedule emerged as the answer.
Now, hybrid work is more than a trend—it is a fundamental shift in how work is structured. It’s transforming offices, redefining team dynamics, and reshaping what “a day at work” really looks like. For companies aiming to attract top talent, reduce overhead, and boost employee satisfaction, understanding this model is not optional—it is essential.
What is a hybrid work schedule?
A hybrid work schedule is a modern work arrangement that allows employees to split their time between working remotely and being present in a physical office. It combines the independence and flexibility of remote work with the structure and collaboration benefits of in-person interactions.
This approach is not about abandoning the office or going fully remote—it’s about designing work around outcomes rather than locations. On some days, employees may work from home, focusing on deep, individual tasks in a distraction-free environment. On others, they might head to the office to brainstorm with colleagues, attend team meetings, or simply reconnect with workplace culture.
Hybrid work schedules can be fixed or flexible. Some companies assign specific in-office days, while others let teams or individuals decide when and where they work best. At its core, the hybrid work model aims to strike the right balance—enabling autonomy without isolation, and collaboration without burnout.
Key characteristics of a hybrid work schedule
While every company may define hybrid work slightly differently, most hybrid work schedules share a few core characteristics. These traits help organizations design flexible systems that work for both the business and its people:
- Dual work modes: Employees divide their time between working remotely (usually from home) and working from a designated office location.
- Structured or flexible schedules: Some models define fixed in-office days, while others allow employees to choose when they come in.
- Task-based location decisions: Deep-focus work is often done remotely, while collaborative or creative tasks are scheduled for in-person days.
- Technology-enabled coordination: Digital tools support scheduling, communication, and productivity regardless of where employees are located.
- Equity and inclusion considerations: Well-structured hybrid models ensure that remote employees have the same access to opportunities, meetings, and information as their in-office peers.
Ultimately, a hybrid work schedule is designed to balance employee autonomy with the benefits of face-to-face collaboration, ensuring that neither flexibility nor teamwork is compromised.
Types of hybrid work schedules
There is no single formula for hybrid work success. The “right” hybrid model varies depending on an organization’s size, culture, industry, and employee needs. Here are the most common types of hybrid schedules used today:

Benefits of a hybrid work schedule
A well-structured hybrid work schedule is not only a perk—it is a performance multiplier. By merging the best of in-office and remote environments, it delivers tangible benefits for both employees and employers.
1. Work-life balance and flexibility
One of the most celebrated advantages of hybrid work is the freedom it offers. Employees can tailor their schedules around peak productivity hours, personal responsibilities, or even daily routines. Skipping the commute on remote days frees up time for family, fitness, or focused work—leading to a healthier and more balanced lifestyle.
2. Increased productivity
When employees have the autonomy to choose their work environment, they’re more likely to deliver better outcomes. Remote days allow for deep, uninterrupted work, while in-office days provide space for collaboration and brainstorming. The result? Higher engagement and output, without the burnout.
3. Better employee retention
Hybrid work schedules appeal to today’s workforce—especially millennials and Gen Z—who prioritize flexibility and autonomy. For working parents, caregivers, or employees with long commutes, hybrid work can be a game-changer. Organizations that embrace this model often see lower attrition rates and higher employee satisfaction, reducing the costly churn of talent.
4. Cost savings for employers
Fewer people in the office each day means lower operational expenses. Companies can downsize real estate, reduce utility bills, and optimize office space through hot desking or shared workstations. In the long run, this can translate into significant savings without sacrificing performance.
5. Cultural and team cohesion
Contrary to popular belief, hybrid work doesn't dilute company culture—it can enrich it. In-office days create opportunities for bonding, mentorship, and collaboration. When planned with intention, these touchpoints help maintain a strong organizational culture while still respecting employees' need for flexibility.
Best practices for hybrid work schedule
Successfully rolling out a hybrid work schedule requires more than simply deciding who works from where. It demands thoughtful planning, open communication, and the right tools. Here are the key best practices to guide a smooth and sustainable implementation:
1. Set clear goals
Before introducing a hybrid model, organizations must define why they’re adopting it. Is the aim to reduce real estate costs? Boost employee satisfaction? Attract remote talent? Having a clear objective ensures that your hybrid strategy aligns with larger business priorities and provides a benchmark to measure success.
2. Involve employees in the design
A top-down approach rarely works when it comes to hybrid scheduling. Survey your employees, hold focus groups, or run pilot programs to understand their needs and preferences. Involving people in the process builds trust, ensures relevance, and improves adoption across departments.
3. Transparent communication of policies
Clarity is everything. Employees need to know when they’re expected in the office, what flexibility they have, and how performance will be measured. Document your hybrid policies clearly and make them easily accessible. Consistent communication helps avoid confusion and perceptions of unfairness.
4. Leverage tools for collaboration and scheduling
Technology is the backbone of any hybrid model. Use platforms that facilitate seamless communication (like Slack or Microsoft Teams), shared calendars, project management tools, and desk-booking systems. The goal is to remove friction, so teams can collaborate effortlessly, whether they’re across the hall or the city.
Smart tools that power a hybrid work schedule
Implementing a hybrid work schedule is more than just policies—it is about giving employees the tools to make flexibility work in real life.
One essential solution is a desk booking system that allows employees to:
- Reserve desks in advance on days they choose to work from the office.
- Check real-time availability to avoid overcrowding or wasted space.
- Coordinate presence with their teammates for smoother collaboration.
- Access intuitive floor maps to choose preferred workstations or zones.
When combined with other smart workplace tools like meeting room scheduling and visitor management, this creates a seamless, stress-free hybrid experience for everyone, from employees to office managers.
Frequently asked questions (FAQs)
Conclusion
Hybrid work is not just a middle ground between remote and in-office work—it is a strategic evolution in how we define productivity, engagement, and workplace culture.
By blending autonomy with collaboration, hybrid work schedules empower employees to do their best work while staying connected to their teams. But to truly unlock the hybrid model’s full potential, companies must implement it with purpose, clarity, and empathy. For organizations navigating the future of work, now is the time to evaluate, design, or refine your hybrid work strategy—because flexibility is no longer a perk; it's a prerequisite.
Ready to embrace the hybrid future?
If you are looking to transition your workplace into a flexible, future-ready environment, now is the time to act. No matter whether you are refining your current policy or building a hybrid work strategy from the ground up, having the right tools and frameworks in place makes all the difference.
Schedule a free demo today!
What is a hybrid work schedule? Benefits, types and best practices
Jun 20, 2025
123
As organizations continue to evolve in the face of changing work patterns, the concept of the modern workplace is undergoing a significant transformation. In this New Era of Physical Workplaces, businesses are not only embracing new technology but also rethinking how office spaces are designed and utilized. The future of workplaces—referred to as Workplace 2.0—rests upon three critical pillars: Infrastructure, People, and Technology. These elements work together to create dynamic, adaptive work environments that foster innovation, collaboration, and productivity.
In this blog, we will explore these three pillars in detail, providing insights into how businesses can integrate them to build future-ready, high-performing workplaces.
The three pillars of modern workplaces
1. Infrastructure: The foundation of a modern workspace
Infrastructure forms the backbone of any office space. It is the physical framework that shapes the experience of employees and visitors alike. A well-thought-out infrastructure is more than just functional; it is strategic, influencing everything from employee well-being to operational efficiency.

The shift towards workplace 2.0 means rethinking traditional office layouts. The days of rigid, closed-off cubicles and large, sterile conference rooms are behind us. In their place, organizations are embracing flexible, open layouts with a focus on creating collaborative spaces and promoting employee engagement.
Key trends in infrastructure for workplace 2.0:
- Flexible office designs: The demand for flexibility has risen as more employees seek adaptable workspaces that can accommodate different work styles. Modular furniture, movable walls, and multi-purpose rooms are all part of this trend, providing employees with a more personalized and agile work environment.
- Sustainability: Green building practices are becoming increasingly important. The integration of eco-friendly materials, energy-efficient systems, and sustainable architecture not only helps reduce costs but also promotes employee well-being by creating healthier workspaces.
- Space utilization: Real-time data gathered from IoT devices enables organizations to monitor how spaces are being used. This data can help optimize layouts, reduce underutilized areas, and enhance the overall office experience for employees.
Impact of infrastructure on the workplace:
- Employee productivity: Studies have found that thoughtfully designed office spaces contribute to enhanced employee performance by fostering a more organized and motivating environment. Access to collaborative spaces, comfortable environments, and efficient layouts leads to a more engaged workforce.
- Enhanced well-being: Modern office designs focus on comfort and wellness, including better air quality, ergonomic furniture, and natural light. These features contribute to improved mental and physical health, ultimately driving performance.
2. Connecting People: The heart of the workplace
While technology and infrastructure play vital roles in creating a successful workplace, it is the people who truly drive its success. The employees' experiences, needs, and behaviors must be at the center of any workplace transformation strategy.

The evolving role of employees in workplace 2.0:
- Hybrid work: The rise of hybrid work models, which combine remote and in-office work, has made it clear that the traditional one-size-fits-all approach no longer works. Employees today desire greater autonomy in choosing their work location and style, allowing them to perform at their best. Achieving the right mix of adaptability and clear frameworks is essential for an effective hybrid work approach.
- Employee experience: In the past, businesses focused on providing a comfortable, functional workspace. Today, employee experience (EX) goes beyond comfort. It embraces career growth, mental health, and social engagement. Organizations that focus on enhancing the employee experience (EX) are more likely to attract high-caliber talent and foster long-term employee loyalty.
- Collaboration and innovation: The physical and digital workspaces need to foster collaboration. Office designs should promote spontaneous interactions, idea-sharing, and creativity. This can be achieved through open spaces, tech-enabled meeting rooms, and employee resource areas designed for team collaboration.
Impact of people-centric workspaces:
- Higher engagement: When employees feel their needs are considered, whether in terms of workspace design, technology, or overall well-being, their engagement levels rise. This translates into higher job satisfaction, better retention rates, and increased productivity.
- Attraction and retention of talent: As younger generations, including millennials and Gen Z, dominate the workforce, their expectations for workplace culture are higher. Employees today look for work environments that reflect their values, providing opportunities for growth, work-life balance, and inclusivity. Workplaces that embrace these priorities are more likely to attract and keep skilled professionals. Workplaces that cater to these expectations will be better equipped to attract and retain top talent.
3. Technology: The catalyst for change
Among the core components of Workplace 2.0, technology stands out as the most impactful force driving change and innovation. The rapid pace of technological innovation is reshaping how work is done, making it more efficient, collaborative, and flexible. In the New Era of Physical Workplaces, smart technology is the enabler that ties together infrastructure and people, creating a seamless, interconnected work environment.

Key technological advancements driving workplace 2.0:
- AI and automation: Artificial Intelligence (AI) is revolutionizing workplace management by automating routine tasks, such as scheduling, resource allocation, and even predictive maintenance of office equipment. By streamlining processes, this not only boosts efficiency but also helps save valuable time across operations.
- IoT (Internet of Things): Modern smart offices are highly dependent on IoT technology to create a connected and responsive work environment. From connected sensors that monitor air quality to smart lighting systems that adjust based on occupancy, IoT enables workplaces to adapt to the needs of the users in real-time. For example, a smart conference room can automatically adjust its lighting, temperature, and equipment based on the number of people attending a meeting.
- Cloud collaboration tools: The growing adoption of cloud collaboration platforms in modern workplaces has played a vital role in enabling seamless communication and productivity, especially in remote and hybrid work environments Tools like Slack, Microsoft Teams, and Zoom enable seamless communication and collaboration across locations, helping teams stay connected and productive no matter where they are working from.
The impact of technology on workplaces:
- Increased efficiency: By automating mundane tasks, technology frees up time for employees to focus on higher-value work. Whether it’s through intelligent office systems or automated workflows, these technologies enhance productivity and streamline operations.
- Improved communication: With a digital-first approach, technology helps bridge gaps in communication, ensuring teams can collaborate effectively regardless of physical distance. This improves not just productivity but also team cohesion.
- Enhanced security: With the integration of smart access control systems and AI-driven surveillance, workplaces are becoming more secure. Technology plays a crucial role in protecting sensitive information and ensuring the safety of employees and visitors.
Conclusion: Building a future-ready workplace
As businesses continue to adapt to the changing work environment, the three pillars of Infrastructure, People, and Technology must work in harmony to create a workplace 2.0 that is efficient, collaborative, and adaptive. The workplace of tomorrow will not only rely on cutting-edge technology but will also be designed with the people who use it in mind.
The New Era of Physical Workplaces is here, and organizations that understand the interdependence of these three pillars will be better positioned to thrive. By investing in flexible infrastructure, prioritizing employee experience, and leveraging technology, companies can create workplaces that inspire innovation, attract top talent, and drive success.
Want to explore more about how these pillars can transform your workplace?
Download the full report, "The New Era of Physical Workplaces," to dive deeper into the trends and technologies shaping the future of workspaces.
The three pillars of modern workplace 2.0: Infrastructure, People, and Technology
Jul 17, 2025
Read time: Loading...
In a world obsessed with cybersecurity, firewalls, and encrypted data, it's easy to forget the most basic threat vector: the front door.
While organizations pour millions into digital protection, physical access remains a critical vulnerability. Who walks into your buildings, labs, or server rooms matters just as much—if not more—than who logs into your network.
A physical access control system (PACS) is a security framework that governs who can enter which physical spaces, and when, ensuring only authorized individuals gain access while everyone else stays out.
More than just locked doors or keycards, PACS is a strategic fusion of hardware, software, and human oversight. It uses sensors, credentials, smart readers, and centralized intelligence to safeguard your real-world assets—from corporate campuses to high-security labs.
Because in current scenario, protecting your people, property, and data starts at the threshold.
What is a physical access control system (PACS)?
A physical access control system (PACS) is a modern security solution designed to manage, monitor, and restrict access to physical locations, from entire buildings to specific rooms or restricted zones. At its core, PACS ensures that only authorized individuals—employees, visitors, or contractors—can enter designated areas, and only at approved times. This fine-tuned control helps prevent breaches, protect sensitive assets, and maintain operational safety.
Unlike traditional locks and keys or manual security checks, a PACS is automated, intelligent, and scalable. It verifies identities using credentials (like keycards, biometrics, or mobile devices), processes them through access rules, and makes real-time decisions—all without the delays or blind spots of human-only systems.
This shift from analog to automated access isn't just a tech upgrade, it is a fundamental transformation in how organizations safeguard the physical side of security.
Key components of a physical access control system
A well-functioning physical access control system (PACS) is built on a network of integrated components, each playing a crucial role in keeping unauthorized individuals out, and authorized ones flowing securely through.
- Access points: These are the physical gateways, doors, turnstiles, gates, or elevators—that the system controls. Each access point becomes a checkpoint where entry is either granted or denied based on credentials.
- Credentials: These are the tools users present to identify themselves:
- Keycards or fobs for swipe or tap access.
- PIN codes entered on a keypad.
- Biometric data like fingerprints or facial scans.
- Smartphones using NFC, Bluetooth, or QR-based mobile credentials Each credential ties back to a specific user profile within the system.

- Readers/scanners: Installed at access points, these devices read the credentials presented by a user and send that data to the control panel for verification. Whether it’s a badge reader, biometric scanner, or mobile QR reader, this is the system’s first contact point.
- Controllers: Often referred to as the “brain” of the system, the controller receives data from the reader, checks authorization rules, and makes the real-time decision to unlock (or deny) the access point. It acts instantly, and logs the event.
- Access control server: This is the central intelligence hub, whether hosted on-premise or in the cloud. It:
- Stores user profiles and access rules
- Manages system configurations
- Logs every access attempt
- Enables remote control and analytics
Modern PACS often favor cloud servers for scalability, multi-site control, and real-time management.
How a physical access control system works ?
A physical access control system operates through a streamlined sequence of actions, each step working behind the scenes to ensure secure, efficient access. Here’s how it all comes together:
1. Authorization: The process begins with administrators assigning access permissions. Each user—whether an employee, contractor, or visitor, is granted customized access based on:
- Who they are
- Where they need to go
- When they’re allowed to enter
Permissions can be as broad or as specific as needed, from 24/7 building-wide access to time-limited entry into one room.
2. Authentication: At the access point (like a door or gate), the user presents their credential—a badge, PIN, fingerprint, or mobile app.
The system verifies that credential against stored data to confirm who the person is.
3. Access decision: Based on the rules defined during authorization, the system immediately decides:
- Grant access and unlock the door
- Deny access and trigger an alert or log the attempt
This decision is made in milliseconds by the system’s controller—removing human error from the equation.
4. Monitoring & logging: Every access attempt successful or not, is recorded. These logs provide:
- An audit trail for investigations or reviews
- Compliance reports for regulated environments
- Real-time alerts for unusual or suspicious activity
5. System integration: Modern PACS can be integrated with other workplace or security systems, including:
- Video surveillance (CCTV)
- Alarm and intrusion detection systems
- Visitor management platforms
- Emergency response protocols
This creates a unified security ecosystem, enhancing visibility, control, and response speed.
When all five steps are working in sync, you get more than just a locked door, you get a dynamic, intelligent access control experience that scales with your security needs.
Common credentials and authentication methods in PACS
PACS can accommodate a wide range of credentials to suit different levels of security, user convenience, and operational needs. Below is a breakdown of the most common authentication methods:

PACS can accommodate a wide range of credentials to suit different levels of security, user convenience, and operational needs. Below is a breakdown of the most common authentication methods:
Why do physical access control systems matter?
Physical access control systems are not just about keeping doors locked—they’re about creating controlled, responsive, and transparent environments where security meets scalability.
Here’s why PACS plays a vital role in safeguarding today’s workplaces:
- Improved security at sensitive touch points: Whether it’s a data center, executive suite, or R&D lab, PACS ensures that only the right people have access, reducing the risk of unauthorized entry, theft, or sabotage.
- User-level control over access rights: PACS allows for granular permission settings, letting administrators define exactly who can go where, and when. Access can be customized by role, department, time of day, or even specific events.
- Full audit trails for compliance: Every access attempt is logged—successes, denials, and anomalies—creating a detailed, time-stamped audit trail that supports internal investigations, regulatory compliance, and operational transparency.
- Remote management through cloud-based systems: Modern PACS platforms allow remote access control, credential updates, and real-time monitoring via web dashboards—ideal for managing multi-site operations or hybrid workforces.
- Integrated ecosystem with other security technologies: PACS can be synced with:
- Video surveillance (CCTV)
- Intrusion detection systems
- Emergency response protocols
- Visitor management tools
This turns your physical access control into a central node of a unified, intelligent security infrastructure. In short, PACS is no longer a nice-to-have, it is a non-negotiable layer of modern security, woven into every door, checkpoint, and access event in your physical environment.
Physical access control systems: Real-world use cases
Physical access control systems are not just security add-ons, they are mission-critical infrastructure across industries where control, compliance, and safety are non-negotiable.
Here’s where PACS is making a real-world impact:
- Corporate offices and headquarters: From managing employee access to executive suites, meeting rooms, or server closets, PACS helps enterprises balance security with flexibility—especially in hybrid work environments.
- Hospitals and clinical zones: Healthcare facilities use PACS to restrict access to ICUs, pharmacies, labs, and patient records. This ensures compliance with health regulations and protects both staff and patients from unauthorized access.
- Government and defense facilities: National security sites require airtight access controls. PACS enables multi-factor authentication, biometric verification, and detailed audit logs—ensuring only vetted personnel can access sensitive zones.
- Data centers and server rooms: For businesses handling large volumes of sensitive data, PACS is essential to secure physical hardware. It also provides traceable logs for compliance with data protection standards like GDPR or HIPAA.
- Hotels, co-living spaces, and gyms: These high-traffic, multi-user environments rely on PACS to manage temporary credentials, guest access, and zone-based permissions—offering convenience without compromising safety.
Frequently asked questions(FAQs)
Conclusion: The gatekeeper of the modern workplace security
In a world where security threats are evolving as fast as technology itself, physical access control systems (PACS) have become a foundational layer of protection, not just for doors and gates, but for data, assets, and people.
By blending physical infrastructure with digital intelligence, PACS empowers organizations to go beyond keys and locks. It provides granular control, real-time monitoring, and seamless integration with broader security systems—all while delivering the scalability and convenience modern workplaces demand.
Whether you’re managing a corporate HQ, a hospital, or a residential complex, the message is clear: it’s time to rethink how access is controlled.
Is your current system secure, scalable, and smart enough?
Now is the time to evaluate your existing access controls and consider upgrading to a modern PACS solution that puts both security and usability at the center.
Because in today’s world, the door isn’t just an entry point—it’s your first line of defense.
Jul 16, 2025
Read time: Loading...
How much of your office space goes unused every single day?
If your answer is anything less than precise, you're not alone—and you're likely leaving money on the table.
As hybrid work becomes the norm and businesses tighten belts in the face of rising real estate costs, the workplace has entered a new era—one that values agility over excess, and efficiency over tradition. Desks sit empty on Fridays, meeting rooms are booked but unused, and facilities teams scramble to make sense of scattered data across spreadsheets, floor plans, and outdated tools.
Enter space management software—the invisible operator behind today’s smartest workplaces. It’s not just about floor plans and seat counts. It’s about reimagining how we use space as a living, dynamic asset—tracked in real time, optimized continuously, and tailored to how your people work. From Fortune 500 campuses to scrappy startups, this tech is quietly transforming the way we think about work environments, making every square foot count.
What is space management software?
Space management software is a digital platform designed to help organizations strategically plan, monitor, and optimize how their physical spaces are used. Whether it’s a bustling office floor, a university campus, or a retail environment, this tool brings visibility, order, and intelligence to every square foot.
At its core, the software manages:
- Physical spaces — from desks and meeting rooms to entire buildings or campuses.
- Occupancy levels — who is using what, when, and how often.
- Resources and assets — furniture, equipment, and shared utilities.
- Booking systems — for rooms, hot desks, or collaboration zones.
It’s tailor-made for today’s dynamic, multi-use environments: hybrid offices, educational institutions, coworking hubs, healthcare facilities, and large enterprises juggling multiple locations.
Unlike traditional tools—think spreadsheets, paper maps, or siloed legacy systems—space management software offers real-time data, interactive floor plans, and automation. That means no more guesswork, no more double-booked rooms, and no more flying blind on occupancy rates. Instead, you're equipped with a single source of truth that evolves with your workplace.
Core functions of space management software
Space management software is not just a digital map of your office—it’s a central command center for how space is used, optimized, and experienced. Here’s what it powers behind the scenes:
- Centralized space data & inventory tracking: Say goodbye to scattered spreadsheets. This software consolidates all your space-related data—available rooms, assigned desks, shared assets, occupancy levels—into one unified dashboard. It’s your single source of truth for smarter decisions.
- Interactive floor plans & space visualization: Visualize your workplace like never before. With interactive floor plans and, in some cases, 3D views, you can see how space is allocated, where teams sit, and what’s underutilized—all in real time. Strategic space planning becomes as easy as drag-and-drop.
- Desk and meeting room booking systems: Enable employees to book spaces with a tap. Whether it’s a hot desk, quiet pod, or huddle room, the system allows seamless self-service reservations synced with your calendar tools. No double bookings. No wasted space. Just frictionless access.

- Real-time occupancy tracking and analytics: Through sensors, badges, or app check-ins, the software captures live usage data—how often rooms are used, which areas are crowded or vacant, and when peak hours hit. With this intel, you can spot patterns, rightsize your space, and plan proactively.
- Move management: Teams, people, and assets: Relocating a team? Shuffling departments? Onboarding new hires? Space management software makes it effortless to reassign desks, move equipment, or redesign entire zones—without the logistical chaos.
- Automation and integrations: Modern platforms integrate with your IoT devices, calendar apps, HR systems, and even building management tools. The result? A fully connected workplace that automates bookings, updates layouts in real time, and keeps everyone in sync—without the manual hustle.
Must have features in a space management software
The best space management tools don’t just show you space—they unlock its full potential. Here are the essential features every modern platform should offer, and why they matter:

Key benefits of using space management software
Beyond floor plans and booking buttons, space management software delivers strategic, measurable impact. Here’s how it pays off—both in real estate and ROI:
- Optimize space utilization: Identify which areas are thriving and which are just collecting dust. Reallocate, repurpose, or retire unused space to get the most out of every square foot.
- Cost savings: Shrink your office footprint, consolidate underused locations, and eliminate inefficiencies in maintenance and operations. Less waste, more value.
- Improve employee experience: Give your people control. With intuitive booking tools and clearer access to the right spaces at the right time, workplace friction drops—and satisfaction rises.
- Scenario planning for growth: Model future space needs, headcount changes, or layout redesigns with data-backed simulations. No guesswork—just strategic foresight.
- Streamline operations: Automate the admin. From booking approvals to occupancy reporting, reduce the manual load so facilities teams can focus on what matters.
- Hybrid-Ready Infrastructure: Support today’s most flexible workstyles. Whether half the team is remote or everyone’s in on Tuesday, your workplace stays organized and optimized.
Space management software: Use cases across industries
Space management software isn not one-size-fits-all—it is a versatile solution powering smarter, more agile environments across sectors. Here’s who’s using it, and why:
- Large enterprises: With sprawling office portfolios and global teams, large organizations rely on space management tools to track occupancy, standardize layouts, and cut down on underused real estate—from HQs to regional hubs.
- Universities and educational campuses: Scheduling classrooms, labs, auditoriums, and event spaces across semesters and departments? These platforms bring order to the chaos—maximizing space and minimizing conflicts across sprawling academic grounds.
- Coworking and flex-space providers: In a world of hot desks and drop-in clients, real-time booking and occupancy visibility are non-negotiable. Space software ensures smooth operations, fair usage, and better customer experience.
- Retail and showrooms: Retailers use it to optimize floor layouts, product displays, and backroom storage. In high-rent locations, every inch matters—and visibility into space usage is key to profitability.
- Healthcare and manufacturing: For facilities with strict compliance needs and high-precision layouts, space management software helps track usage, meet regulatory standards, and ensure smooth movement of people, equipment, and processes.
Frequently ssked questions (FAQs)
Conclusion: Future-proofing the modern workspace
Space is no longer just square footage—it is a strategic asset. And space management software is the engine that ensures every inch is working as hard as your people do.
By delivering real-time visibility, smarter resource allocation, and seamless workplace experiences, this technology transforms how organizations operate—cutting costs, boosting productivity, and enabling agility in a hybrid-first world.
In an era where flexibility is currency and real estate is under the microscope, space management software isn’t a nice-to-have. It’s the blueprint for future-ready workplaces.
Now’s the time to ask: Are you using your space, or is it using you?
Take the first step—audit your space usage and uncover the hidden value in your workplace.
Jul 4, 2025
Read time: Loading...
In today’s ever-evolving world of work, one term continues to dominate boardroom conversations and HR strategy decks: hybrid work schedule.
Born out of necessity during the COVID-19 pandemic and refined through ongoing experimentation, the hybrid model has become the blueprint for how modern organizations operate. As businesses reopened physical offices, the one-size-fits-all approach to work—commuting five days a week—no longer made sense. Employees wanted flexibility. Employers wanted productivity and culture. The hybrid schedule emerged as the answer.
Now, hybrid work is more than a trend—it is a fundamental shift in how work is structured. It’s transforming offices, redefining team dynamics, and reshaping what “a day at work” really looks like. For companies aiming to attract top talent, reduce overhead, and boost employee satisfaction, understanding this model is not optional—it is essential.
What is a hybrid work schedule?
A hybrid work schedule is a modern work arrangement that allows employees to split their time between working remotely and being present in a physical office. It combines the independence and flexibility of remote work with the structure and collaboration benefits of in-person interactions.
This approach is not about abandoning the office or going fully remote—it’s about designing work around outcomes rather than locations. On some days, employees may work from home, focusing on deep, individual tasks in a distraction-free environment. On others, they might head to the office to brainstorm with colleagues, attend team meetings, or simply reconnect with workplace culture.
Hybrid work schedules can be fixed or flexible. Some companies assign specific in-office days, while others let teams or individuals decide when and where they work best. At its core, the hybrid work model aims to strike the right balance—enabling autonomy without isolation, and collaboration without burnout.
Key characteristics of a hybrid work schedule
While every company may define hybrid work slightly differently, most hybrid work schedules share a few core characteristics. These traits help organizations design flexible systems that work for both the business and its people:
- Dual work modes: Employees divide their time between working remotely (usually from home) and working from a designated office location.
- Structured or flexible schedules: Some models define fixed in-office days, while others allow employees to choose when they come in.
- Task-based location decisions: Deep-focus work is often done remotely, while collaborative or creative tasks are scheduled for in-person days.
- Technology-enabled coordination: Digital tools support scheduling, communication, and productivity regardless of where employees are located.
- Equity and inclusion considerations: Well-structured hybrid models ensure that remote employees have the same access to opportunities, meetings, and information as their in-office peers.
Ultimately, a hybrid work schedule is designed to balance employee autonomy with the benefits of face-to-face collaboration, ensuring that neither flexibility nor teamwork is compromised.
Types of hybrid work schedules
There is no single formula for hybrid work success. The “right” hybrid model varies depending on an organization’s size, culture, industry, and employee needs. Here are the most common types of hybrid schedules used today:

Benefits of a hybrid work schedule
A well-structured hybrid work schedule is not only a perk—it is a performance multiplier. By merging the best of in-office and remote environments, it delivers tangible benefits for both employees and employers.
1. Work-life balance and flexibility
One of the most celebrated advantages of hybrid work is the freedom it offers. Employees can tailor their schedules around peak productivity hours, personal responsibilities, or even daily routines. Skipping the commute on remote days frees up time for family, fitness, or focused work—leading to a healthier and more balanced lifestyle.
2. Increased productivity
When employees have the autonomy to choose their work environment, they’re more likely to deliver better outcomes. Remote days allow for deep, uninterrupted work, while in-office days provide space for collaboration and brainstorming. The result? Higher engagement and output, without the burnout.
3. Better employee retention
Hybrid work schedules appeal to today’s workforce—especially millennials and Gen Z—who prioritize flexibility and autonomy. For working parents, caregivers, or employees with long commutes, hybrid work can be a game-changer. Organizations that embrace this model often see lower attrition rates and higher employee satisfaction, reducing the costly churn of talent.
4. Cost savings for employers
Fewer people in the office each day means lower operational expenses. Companies can downsize real estate, reduce utility bills, and optimize office space through hot desking or shared workstations. In the long run, this can translate into significant savings without sacrificing performance.
5. Cultural and team cohesion
Contrary to popular belief, hybrid work doesn't dilute company culture—it can enrich it. In-office days create opportunities for bonding, mentorship, and collaboration. When planned with intention, these touchpoints help maintain a strong organizational culture while still respecting employees' need for flexibility.
Best practices for hybrid work schedule
Successfully rolling out a hybrid work schedule requires more than simply deciding who works from where. It demands thoughtful planning, open communication, and the right tools. Here are the key best practices to guide a smooth and sustainable implementation:
1. Set clear goals
Before introducing a hybrid model, organizations must define why they’re adopting it. Is the aim to reduce real estate costs? Boost employee satisfaction? Attract remote talent? Having a clear objective ensures that your hybrid strategy aligns with larger business priorities and provides a benchmark to measure success.
2. Involve employees in the design
A top-down approach rarely works when it comes to hybrid scheduling. Survey your employees, hold focus groups, or run pilot programs to understand their needs and preferences. Involving people in the process builds trust, ensures relevance, and improves adoption across departments.
3. Transparent communication of policies
Clarity is everything. Employees need to know when they’re expected in the office, what flexibility they have, and how performance will be measured. Document your hybrid policies clearly and make them easily accessible. Consistent communication helps avoid confusion and perceptions of unfairness.
4. Leverage tools for collaboration and scheduling
Technology is the backbone of any hybrid model. Use platforms that facilitate seamless communication (like Slack or Microsoft Teams), shared calendars, project management tools, and desk-booking systems. The goal is to remove friction, so teams can collaborate effortlessly, whether they’re across the hall or the city.
Smart tools that power a hybrid work schedule
Implementing a hybrid work schedule is more than just policies—it is about giving employees the tools to make flexibility work in real life.
One essential solution is a desk booking system that allows employees to:
- Reserve desks in advance on days they choose to work from the office.
- Check real-time availability to avoid overcrowding or wasted space.
- Coordinate presence with their teammates for smoother collaboration.
- Access intuitive floor maps to choose preferred workstations or zones.
When combined with other smart workplace tools like meeting room scheduling and visitor management, this creates a seamless, stress-free hybrid experience for everyone, from employees to office managers.
Frequently asked questions (FAQs)
Conclusion
Hybrid work is not just a middle ground between remote and in-office work—it is a strategic evolution in how we define productivity, engagement, and workplace culture.
By blending autonomy with collaboration, hybrid work schedules empower employees to do their best work while staying connected to their teams. But to truly unlock the hybrid model’s full potential, companies must implement it with purpose, clarity, and empathy. For organizations navigating the future of work, now is the time to evaluate, design, or refine your hybrid work strategy—because flexibility is no longer a perk; it's a prerequisite.
Ready to embrace the hybrid future?
If you are looking to transition your workplace into a flexible, future-ready environment, now is the time to act. No matter whether you are refining your current policy or building a hybrid work strategy from the ground up, having the right tools and frameworks in place makes all the difference.
Schedule a free demo today!
Jun 20, 2025
Read time: Loading...
As organizations continue to evolve in the face of changing work patterns, the concept of the modern workplace is undergoing a significant transformation. In this New Era of Physical Workplaces, businesses are not only embracing new technology but also rethinking how office spaces are designed and utilized. The future of workplaces—referred to as Workplace 2.0—rests upon three critical pillars: Infrastructure, People, and Technology. These elements work together to create dynamic, adaptive work environments that foster innovation, collaboration, and productivity.
In this blog, we will explore these three pillars in detail, providing insights into how businesses can integrate them to build future-ready, high-performing workplaces.
The three pillars of modern workplaces
1. Infrastructure: The foundation of a modern workspace
Infrastructure forms the backbone of any office space. It is the physical framework that shapes the experience of employees and visitors alike. A well-thought-out infrastructure is more than just functional; it is strategic, influencing everything from employee well-being to operational efficiency.

The shift towards workplace 2.0 means rethinking traditional office layouts. The days of rigid, closed-off cubicles and large, sterile conference rooms are behind us. In their place, organizations are embracing flexible, open layouts with a focus on creating collaborative spaces and promoting employee engagement.
Key trends in infrastructure for workplace 2.0:
- Flexible office designs: The demand for flexibility has risen as more employees seek adaptable workspaces that can accommodate different work styles. Modular furniture, movable walls, and multi-purpose rooms are all part of this trend, providing employees with a more personalized and agile work environment.
- Sustainability: Green building practices are becoming increasingly important. The integration of eco-friendly materials, energy-efficient systems, and sustainable architecture not only helps reduce costs but also promotes employee well-being by creating healthier workspaces.
- Space utilization: Real-time data gathered from IoT devices enables organizations to monitor how spaces are being used. This data can help optimize layouts, reduce underutilized areas, and enhance the overall office experience for employees.
Impact of infrastructure on the workplace:
- Employee productivity: Studies have found that thoughtfully designed office spaces contribute to enhanced employee performance by fostering a more organized and motivating environment. Access to collaborative spaces, comfortable environments, and efficient layouts leads to a more engaged workforce.
- Enhanced well-being: Modern office designs focus on comfort and wellness, including better air quality, ergonomic furniture, and natural light. These features contribute to improved mental and physical health, ultimately driving performance.
2. Connecting People: The heart of the workplace
While technology and infrastructure play vital roles in creating a successful workplace, it is the people who truly drive its success. The employees' experiences, needs, and behaviors must be at the center of any workplace transformation strategy.

The evolving role of employees in workplace 2.0:
- Hybrid work: The rise of hybrid work models, which combine remote and in-office work, has made it clear that the traditional one-size-fits-all approach no longer works. Employees today desire greater autonomy in choosing their work location and style, allowing them to perform at their best. Achieving the right mix of adaptability and clear frameworks is essential for an effective hybrid work approach.
- Employee experience: In the past, businesses focused on providing a comfortable, functional workspace. Today, employee experience (EX) goes beyond comfort. It embraces career growth, mental health, and social engagement. Organizations that focus on enhancing the employee experience (EX) are more likely to attract high-caliber talent and foster long-term employee loyalty.
- Collaboration and innovation: The physical and digital workspaces need to foster collaboration. Office designs should promote spontaneous interactions, idea-sharing, and creativity. This can be achieved through open spaces, tech-enabled meeting rooms, and employee resource areas designed for team collaboration.
Impact of people-centric workspaces:
- Higher engagement: When employees feel their needs are considered, whether in terms of workspace design, technology, or overall well-being, their engagement levels rise. This translates into higher job satisfaction, better retention rates, and increased productivity.
- Attraction and retention of talent: As younger generations, including millennials and Gen Z, dominate the workforce, their expectations for workplace culture are higher. Employees today look for work environments that reflect their values, providing opportunities for growth, work-life balance, and inclusivity. Workplaces that embrace these priorities are more likely to attract and keep skilled professionals. Workplaces that cater to these expectations will be better equipped to attract and retain top talent.
3. Technology: The catalyst for change
Among the core components of Workplace 2.0, technology stands out as the most impactful force driving change and innovation. The rapid pace of technological innovation is reshaping how work is done, making it more efficient, collaborative, and flexible. In the New Era of Physical Workplaces, smart technology is the enabler that ties together infrastructure and people, creating a seamless, interconnected work environment.

Key technological advancements driving workplace 2.0:
- AI and automation: Artificial Intelligence (AI) is revolutionizing workplace management by automating routine tasks, such as scheduling, resource allocation, and even predictive maintenance of office equipment. By streamlining processes, this not only boosts efficiency but also helps save valuable time across operations.
- IoT (Internet of Things): Modern smart offices are highly dependent on IoT technology to create a connected and responsive work environment. From connected sensors that monitor air quality to smart lighting systems that adjust based on occupancy, IoT enables workplaces to adapt to the needs of the users in real-time. For example, a smart conference room can automatically adjust its lighting, temperature, and equipment based on the number of people attending a meeting.
- Cloud collaboration tools: The growing adoption of cloud collaboration platforms in modern workplaces has played a vital role in enabling seamless communication and productivity, especially in remote and hybrid work environments Tools like Slack, Microsoft Teams, and Zoom enable seamless communication and collaboration across locations, helping teams stay connected and productive no matter where they are working from.
The impact of technology on workplaces:
- Increased efficiency: By automating mundane tasks, technology frees up time for employees to focus on higher-value work. Whether it’s through intelligent office systems or automated workflows, these technologies enhance productivity and streamline operations.
- Improved communication: With a digital-first approach, technology helps bridge gaps in communication, ensuring teams can collaborate effectively regardless of physical distance. This improves not just productivity but also team cohesion.
- Enhanced security: With the integration of smart access control systems and AI-driven surveillance, workplaces are becoming more secure. Technology plays a crucial role in protecting sensitive information and ensuring the safety of employees and visitors.
Conclusion: Building a future-ready workplace
As businesses continue to adapt to the changing work environment, the three pillars of Infrastructure, People, and Technology must work in harmony to create a workplace 2.0 that is efficient, collaborative, and adaptive. The workplace of tomorrow will not only rely on cutting-edge technology but will also be designed with the people who use it in mind.
The New Era of Physical Workplaces is here, and organizations that understand the interdependence of these three pillars will be better positioned to thrive. By investing in flexible infrastructure, prioritizing employee experience, and leveraging technology, companies can create workplaces that inspire innovation, attract top talent, and drive success.
Want to explore more about how these pillars can transform your workplace?
Download the full report, "The New Era of Physical Workplaces," to dive deeper into the trends and technologies shaping the future of workspaces.
Jun 11, 2025
Read time: Loading...
Workplace stress is on the rise—and the numbers speak for themselves. According to the American Institute of Stress, nearly 83% of U.S. workers report feeling stressed by at least one aspect of their job. Additionally, it's estimated that over 1 million workers are absent each day due to stress-related conditions.
As the pace of work accelerates and boundaries between personal and professional life continue to blur, managing stress in the workplace has become not just important—but essential. Unchecked stress affects productivity, well-being, and company culture, often leading to burnout, disengagement, and high turnover.
In this blog, we explore the urgent need for effective workplace stress management and outline 5 practical, research-backed strategies to help create healthier, more focused, and more resilient teams.
Why managing stress in the workplace matters?
Stress at work is not just about feeling tired or overwhelmed. It can make it harder to focus, cause more mistakes, and lead to more sick days. The World Health Organization (WHO) says that stress at work costs businesses around $1 trillion each year because people are not able to do their best.
Some jobs come with extra pressure. People who work in security, administration, or operations often have long hours, tight schedules, and a lot of responsibility. They need to solve problems quickly, stay alert, and talk to many people throughout the day. This kind of work can make stress build up quickly.
A study by NIOSH found that 4 out of 10 workers feel very stressed at their job, and almost 3 out of 10 feel stressed most of the time .
When stress is not managed well, people feel more tired, miss more work, and find it harder to stay motivated. This is why it is important for workplaces to support employees and help them manage stress in healthy ways.
5 strategies to manage stress in the workplace
1. Encourage open communication
Letting people speak up and share their thoughts helps reduce stress. When employees feel heard, they worry less and feel more supported. Team check-ins, anonymous surveys, and open-door policies give everyone a chance to speak honestly.
2. Redesign workspaces for calm and focus
The way an office looks and feels can change how people feel at work. Natural light, quiet zones, and clean spaces make it easier to focus and stay calm. Simple changes—like adding plants or using noise-free areas—can help reduce stress. Smart workplace solutions can help manage meeting room bookings and create calm, distraction-free zones.
3. Offer mental wellness tools (e.g., meditation apps, quiet rooms)
Giving employees tools to care for their mental health shows that the company cares. Things like meditation apps, wellness challenges, or a quiet room can help people take short breaks and relax during the day.
4. Enable workload visibility with task management tools
When people know what they need to do and when to do it, they feel more in control. Task management tools help everyone stay on the same page and avoid last-minute stress. In workplace workplace dashboards, teams can see workloads clearly and plan better together.
5. Recognize and reward efforts regularly
Saying “thank you” or celebrating small wins can really boost someone’s mood. When employees feel appreciated, they feel less pressure and more motivation. Even simple things like shout-outs in team meetings or rewards for good work can go a long way.

Workplace stress management tools
Workplace stress management is not only about wellness programs or team check-ins—it also involves using the right tools to understand and improve the work environment. Digital technology can help track stress levels, improve how spaces are used, and give employees more control over their day.
One helpful area is scheduling tools. These allow employees to plan their day better by showing meetings, tasks, and free time in one place. When people can see their schedule clearly, they feel more prepared and less rushed.
Another useful solution is space management software. These tools show which rooms are free, which areas are crowded, and how often shared spaces are used. This helps reduce stress by making sure people have access to quiet rooms, meeting areas, or break spaces when they need them. It also avoids last-minute scrambles to find space to work or meet.
Occupancy insights are another key feature. They show how many people are in a certain area at a given time. This helps leaders understand where people might feel overwhelmed or distracted. If one space is always full and noisy, changes can be made—like opening new rooms or creating calm zones.
Together, these tools help managers spot early signs of stress and give employees more control over how they work. With better planning and smarter space use, the entire team can feel more focused, supported, and calm throughout the day. This is what makes digital tools such a powerful part of workplace stress management.
Managing workplace stress as a leader
Managing workplace stress is an important part of leadership. Security leads, facility managers, and team supervisors can make a big difference by noticing stress early and supporting their teams in the right way.
How to recognize stress signals?
Look for signs that someone may be feeling stressed:
- They seem tired or low on energy.
- They are quieter or less social than usual.
- They miss deadlines or make more mistakes
- They take more sick days or ask for time off.
- Their mood or behavior has suddenly changed.
These signs can be easy to miss, so regular check-ins are helpful.
How to build a supportive environment?
Leaders can take simple steps to create a culture of care:
- Ask how team members are doing—not just about work, but how they feel.
- Encourage open talks without fear of judgment.
- Respect break times and days off so people can recharge.
- Model calm behavior during stressful times to set the tone.
When people feel safe to speak up, ask for help, or share feedback, it creates psychological safety—a key part of managing workplace stress.
Why does it matters?
When leaders take action:
- Teams feel supported and perform better.
- Stress does not build up unnoticed.
- The workplace becomes healthier and more positive.
Good leadership means making sure no one feels alone in their stress—and that help is always within reach.
Frequently asked questions (FAQs)
Conclusion
Reducing stress at work is not just a nice-to-have—it is a must for keeping teams healthy, focused, and happy. When stress is managed well, employees can do their best work and feel more supported every day.
Leaders play a big role in this. Now is a great time to take a closer look at your workplace. Are there clear schedules? Do your teams have quiet spaces? Is there room for open conversation?
A quick check of daily routines and tools can uncover easy ways to lower stress across the board.
Connect with our workplace experts and explore how to create stress-free, productive workplaces for hybrid and frontline teams.
Jun 6, 2025
Read time: Loading...
The rise of hybrid workforces is reshaping modern workplaces, nearly 73% of U.S. employees now work in a hybrid setting, and this trend is only accelerating. As businesses navigate this shift, creating an effective workplace experience has never been more critical. Hybrid teams, where some employees are working remotely and others in the office, face unique challenges in staying aligned, productive, and engaged. The success of these teams relies heavily on how well communication, collaboration, and company culture are maintained across different environments. The question becomes: How can organizations ensure their hybrid teams thrive in this new dynamic?
This blog will explore key strategies that can significantly enhance the workplace experience for hybrid teams. We will delve into the importance of balancing technology, communication, company culture, and employee well-being to create a productive and engaging work environment for all team members, regardless of their location. By leveraging the right tools, fostering a culture of trust, and providing flexibility, businesses can ensure that their hybrid workforce not only survives but thrives in today’s ever-evolving landscape.
Strategies to improve workplace experience
1. Centralized communication and collaboration
Hybrid teams often face the challenge of disjointed communication. With some team members working from the office and others remotely, it’s easy for information silos to develop, leading to confusion, missed updates, and decreased productivity. Without clear communication channels, employees may feel disconnected from the team, leading to reduced engagement and a lack of alignment on key projects. In a hybrid work environment, it’s essential to centralize communication to ensure that all team members, regardless of their physical location, are on the same page.
Centralizing communication enables hybrid teams to work more cohesively, facilitating smooth workflows and ensuring that everyone feels included. By using a unified platform for all communications, document sharing, and project management, businesses can reduce confusion and enhance overall team collaboration.
Best Practices:
- A unified platform: Smart workplace platforms centralize communications, share files, and manage projects. These platforms integrate multiple functions—messaging, document storage, and task management—into a single, accessible place, allowing teams to stay organized and connected.
- Support asynchronous work: Not all hybrid teams work on the same schedule, so it’s crucial to support asynchronous work. Ensure that the teams can utilize tools such as discussion boards, task comments, and recorded video messages, which allow members in different time zones or with varying schedules to contribute meaningfully without the need for simultaneous presence. This approach ensures that everyone, whether in the office or working remotely, has an opportunity to contribute effectively.
2. Redesign physical and digital workspaces
In a hybrid work environment, creating spaces that accommodate both onsite and remote employees is essential for fostering engagement, collaboration, and a strong company culture. A well-designed workspace can bridge the gap between employees working in the office and those working remotely. By ensuring that both groups have access to the tools, resources, and spaces needed for effective communication and collaboration, organizations can create an inclusive environment that strengthens team cohesion and productivity.
Workspace design goes beyond just physical layouts; it encompasses digital tools and virtual environments that enable seamless interaction. Hybrid teams need both well-thought-out office spaces for in-person collaboration and robust digital workspaces that facilitate easy communication for remote employees. By focusing on both physical and digital workspaces, businesses can create an environment that supports collaboration and ensures no team member is left behind.
Best practices:
- Redesign office layouts: To foster better interaction and engagement among onsite employees, consider designing open spaces and flexible seating arrangements that encourage collaboration and creativity. Additionally, larger meeting rooms equipped with advanced technology for video conferencing allow hybrid meetings to take place smoothly, making it easier for remote workers to participate in discussions and brainstorm sessions.
- Use workplace experience apps: Apps like Veris can help employees plan their time in the office by providing real-time updates on office occupancy. These apps allow employees to see who is in the office on any given day, helping them plan collaborative sessions and meetings accordingly. Such tools ensure that employees have a clear understanding of when and where they can meet with colleagues onsite, streamlining the hybrid collaboration process.
- Provide wellness amenities: To support employees physical and mental well-being, integrate wellness spaces into office design, such as gyms, kitchens, and quiet zones. These spaces allow employees to take breaks, recharge, and stay healthy while at work. Additionally, offering wellness workshops both in-person and virtually can help employees feel more connected and supported in both their personal and professional lives. By prioritizing well-being, organizations can improve overall employee satisfaction and retention.
3. Foster a culture of trust and autonomy
In a hybrid work environment, trust is the foundation of a high-performing and motivated team. When employees feel trusted by their managers and organization, they are more likely to take ownership of their work, manage their time effectively, and deliver high-quality results. Trust also fosters a sense of autonomy, which empowers employees to make decisions, take initiative, and develop innovative solutions. A culture built on trust encourages accountability and responsibility, ensuring that employees are committed to achieving organizational goals without micromanagement.
Trust is especially important in hybrid teams, where employees may not have the same level of direct supervision as in traditional office settings. By focusing on outcomes rather than hours worked, organizations can create an environment that values results over activity, giving employees the freedom to balance their work and personal lives while still meeting expectations.
Best practices:
- Focus on outcomes achieved: Shift the focus from tracking hours worked to measuring the outcomes employees achieve. Allow employees to manage their schedules and work at times that best suit them, while ensuring they meet deliverables and key performance metrics. This approach encourages employees to be more results-driven, and it helps maintain motivation and job satisfaction.
- Collect regular feedback: Create channels for employees to provide feedback, whether through formal surveys, quick polls, or informal check-ins. When employees feel that their voices are heard and their opinions are valued, they are more likely to feel connected to the organization and motivated to contribute. Regular feedback also helps to identify areas for improvement, ensuring that the company is aligned with employees’ needs and expectations.
4. Make meetings inclusive and effective
A major challenge in hybrid teams is ensuring that meetings are inclusive for both onsite and remote workers. In a traditional office setting, it’s easier to hold meetings where all team members are in the same room. However, in a hybrid environment, remote employees may feel disconnected or sidelined if meetings aren’t designed with their inclusion in mind. It’s crucial to make meetings accessible, engaging, and productive for everyone, regardless of their physical location. Well-structured and inclusive meetings not only improve productivity but also foster a sense of team unity and engagement.
Best Practices:
- Share meeting agendas in advance: To ensure that all participants are prepared and can contribute meaningfully, share the meeting agenda ahead of time. This allows remote employees to review the topics and gather any necessary information before the meeting begins, making the session more efficient and focused.
- Ensure audio and video accessibility: Use technology to ensure audio and video accessibility for everyone in the meeting. This includes investing in high-quality video conferencing tools, microphones, and cameras to ensure clear communication for both onsite and remote participants. Setting up virtual meeting rooms where all employees feel included and heard can significantly improve the meeting experience for remote workers.
- Record meetings and share notes afterward: Not everyone can attend meetings at the same time, especially in hybrid teams where some employees may be working in different time zones. Recording meetings and sharing meeting notes afterward ensures that no one misses out on important information. This also provides an opportunity for team members to revisit discussions and follow up on any action items.
5. Encourage social connection and recognition
Building a strong team culture is crucial for remote and hybrid teams, where employees may not have the chance to interact face-to-face as often. Informal interactions and recognition play a vital role in making team members feel connected, valued, and motivated. Encouraging social bonding, even in a virtual setting, helps prevent feelings of isolation and fosters a sense of camaraderie and belonging. Additionally, regular recognition for both small wins and significant achievements reinforces a positive culture, boosts employee morale, and improves overall engagement.
Best Practices:
- Create virtual spaces for socializing: Set up virtual hangouts, hobby groups, or informal chat rooms where employees can unwind and connect on a personal level. These spaces help replicate the spontaneous interactions that occur in traditional office settings and promote social bonding.
- Celebrate milestones, birthdays, and work achievements: Even in a hybrid setting, it’s important to celebrate both personal and professional milestones. Organize virtual events to celebrate birthdays, work anniversaries, and team achievements. Publicly acknowledging employees' efforts helps foster a culture of appreciation and strengthens team relationships.
- Implement recognition programs: Develop both formal (e.g., monthly awards, employee of the month) and informal (e.g., personalized thank-you emails, shout-outs during team meetings) recognition programs. Recognizing achievements, no matter how big or small, motivates employees, reinforces positive behaviors, and strengthens team cohesion.
6. Offer flexibility with a clear structure
In a hybrid work environment, flexibility is essential for maintaining work-life balance and ensuring employees can work at their best. However, while flexibility is important, it needs to be paired with clear expectations and structure to maintain productivity and accountability. The balance between offering flexible working hours and ensuring team alignment through core hours and defined deadlines is crucial to ensure that hybrid teams remain engaged, focused, and collaborative.
Best Practices:
- Allow employees to set flexible working hours: Trust employees to manage their schedules while ensuring they meet deadlines and deliverables. Set core hours for collaboration and meetings to ensure that all team members are available at overlapping times for discussion and collaboration. This flexibility not only accommodates different time zones but also allows employees to balance personal commitments with work.
- Use shared task boards: Leverage task management tools like Kanban boards or Trello to visualize project progress, deadlines, and individual responsibilities. This ensures that all team members are on the same page and can easily track the status of various tasks. Task boards also help prioritize work and avoid bottlenecks, ensuring that deadlines are met without overwhelming any single team member.
7. Invest in technology and workplace security
For hybrid teams, technology plays a central role in enabling seamless collaboration and ensuring that employees can work effectively from any location. However, with remote work comes the need for heightened security to protect sensitive company data. By investing in the right digital tools and implementing strong security measures, companies can empower their hybrid teams to work efficiently while safeguarding critical information from cyber threats.
Best Practices:
- Equip teams with the right digital tools: Provide employees with the necessary tools to collaborate, brainstorm, and manage tasks effectively. Veris provides a complete suite of tools for communication, project management, and collaboration that keep hybrid teams productive and secure. This facilitates real-time collaboration, ensuring that all team members can contribute effectively.
- Implement strong cybersecurity measures: Protect sensitive information by implementing secure access protocols, data encryption, and multi-factor authentication. Regularly train employees on cybersecurity best practices to ensure that they understand how to protect company data and maintain compliance with privacy regulations.
8. Promote professional growth and well-being
For hybrid teams to remain engaged and motivated, it’s crucial to offer continuous opportunities for both professional growth and personal well-being. Remote and hybrid workforces often miss out on in-person development opportunities, so organizations must create virtual or flexible options to support continuous learning and employee wellness. Supporting professional growth through training, mentorship, and career development ensures that employees feel valued and invested in, while promoting well-being helps maintain high productivity and mental health.
Best Practices:
- Provide access to online courses, mentorship programs, and lunch-and-learn sessions: Hybrid teams benefit from continuous learning opportunities, such as online courses on platforms like Udemy or LinkedIn Learning. Offering mentorship programs and lunch-and-learn sessions, where employees can participate in educational webinars or discussions, helps employees grow professionally and stay motivated. These opportunities can be tailored to employee roles and interests, helping them advance in their careers.
- Encourage ergonomic home office setups: Promote employee well-being by offering stipends or resources to create ergonomically friendly home offices. This can include providing employees with funds to purchase comfortable chairs, desks, or equipment that ensures they are physically comfortable while working from home. An ergonomic setup not only reduces physical strain but also boosts productivity and mental well-being.
9. Regularly assess and adapt
Hybrid work environments are inherently dynamic, with employee needs and business objectives constantly evolving. To ensure ongoing success, organizations must regularly assess and adapt their hybrid work strategies. Gathering feedback and making data-driven adjustments based on employee experiences ensures that the hybrid model remains effective and aligns with company goals. Regular evaluation helps prevent stagnation and keeps the workplace environment inclusive, engaging, and efficient for all employees.
Best Practices:
- Continuously gather feedback through surveys and open discussions: Use tools like surveys, focus groups, or informal check-ins to collect feedback from employees on their experiences with the hybrid model. Understanding what’s working and what isn’t allows companies to make informed adjustments to policies, technology, or processes. This continuous feedback loop ensures that employees feel heard and that their needs are addressed in real-time.
- Be open to adapting hybrid work policies: Hybrid work strategies should evolve as employee expectations change and as companies adapt to new challenges. Companies should be prepared to update work-from-home policies, collaboration tools, and even work hours based on employee feedback and emerging trends. This adaptability helps maintain a highly responsive workplace where employees feel supported and empowered.

Frequently asked questions (FAQs)
Conclusion
As hybrid work becomes the new normal, organizations must adapt to ensure their teams stay connected, productive, and engaged. By implementing strategies that prioritize communication, collaboration, trust, and employee well-being, businesses can create a workplace experience that supports both remote and onsite employees. With, a smart workplace platform, organizations can streamline their hybrid work strategies, making it easier to manage communication, collaboration, and employee engagement from anywhere.
From redesigning physical and digital workspaces to fostering a culture of flexibility and trust, these strategies are key to thriving in a hybrid environment. Embracing technology that facilitates seamless collaboration and prioritizing employee well-being will ensure that both individual team members and the organization continue to thrive in today’s dynamic workplace.
Ready to enhance workplace experience of your hybrid team?
We offer a comprehensive suite of smart workplace solutions designed to improve collaboration, streamline communication, and enhance employee well-being for hybrid teams.
Schedule a demo or connect to our workplace experts and start optimizing your workplace today. Ensure that your teams stay engaged, productive, and connected—whether they are working remotely or onsite.
Jun 5, 2025
Read time: Loading...
Time is the only resource in the workplace that cannot be replenished—once it's gone, it’s gone. In fast-paced professional environments where deadlines are tight and demands are high, how employees choose to spend their time directly shapes both personal performance and organizational success.
An integrated smart workplace platform, helps businesses optimize time management by providing tools for efficient communication, collaboration, and resource management, ensuring that both teams and individuals can maximize their productivity.
What is time management at workplace?
Time management in the workplace refers to the ability to plan, prioritize, and execute tasks efficiently within a set timeframe. It's about making conscious decisions to optimize working hours, minimize distractions, and allocate effort where it matters most.
When mastered, time management becomes more than just a productivity hack—it is a foundational skill that drives higher output, improves mental well-being, strengthens team collaboration, and fuels long-term business growth.
The benefits of time management at workplace
1. Increased productivity and efficiency
Effective time management helps employees focus on high-impact tasks rather than getting caught up in reactive or low-priority work. By identifying what's urgent and important, professionals can channel their energy toward meaningful output—completing more work in less time without sacrificing quality.
According to a ProofHub study, companies that implement structured time management practices see up to a 25% increase in productivity, proving that better planning leads to better performance.
2. Consistent on-time delivery
Meeting deadlines isn’t just about speed—it’s about structure. When employees use techniques like time-blocking, task batching, or calendar scheduling, they create a roadmap for success. This reduces last-minute scrambles and builds a culture of reliability and accountability.
Tools like Google Calendar or project management platforms such as Trello and Asana help ensure that deliverables stay on track and expectations are consistently met.
3. Improved quality of work
Rushed work is rarely good work. Time management gives employees the space to focus deeply on complex tasks, minimizing errors and enhancing the overall quality of output. By allocating uninterrupted time for critical work, Veris helps professionals to stay organized, making it easier to maintain high-quality standards.
High-priority tasks receive the attention they deserve, resulting in deliverables that meet or exceed expectations.
4. Reduced stress and anxiety
A cluttered schedule leads to a cluttered mind. When employees feel overwhelmed by competing deadlines and unclear priorities, stress builds up quickly. But with effective time planning, they regain control over their workload.
Research by Deel shows that employees who manage their time well report significantly lower levels of workplace anxiety and burnout—making mental well-being one of the biggest hidden wins of time management.
5. Better decision-making
Good decisions require time to think. When employees are constantly reacting to urgent tasks, they don’t have the bandwidth to assess options or consider long-term impacts. Time management allows room for thoughtful analysis and informed action.
Instead of making knee-jerk decisions under pressure, professionals who manage their time effectively are able to weigh options, seek input, and choose wisely.
6. Enhanced work-life balance
When time is managed effectively during working hours, employees can truly “clock out” at the end of the day without the nagging feeling of unfinished tasks. This separation between professional responsibilities and personal life fosters a healthier routine and more restorative downtime.
A strong work-life balance contributes to higher job satisfaction, better mental health, and improved employee retention—making it a win for both individuals and organizations.
7. Reduced procrastination
Procrastination isn’t just laziness—it’s often a sign of feeling overwhelmed. Time management offers a solution by breaking large, intimidating projects into manageable steps with clear deadlines. This structured approach helps reduce avoidance behavior and encourages steady, rewarding progress.
Micro-tasking and setting short, achievable goals create dopamine-driven momentum, making it easier to start and finish what once felt daunting.
8. Improved job satisfaction and career growth
The more effectively someone manages their time, the more they accomplish—and those accomplishments build confidence. When employees consistently meet goals, exceed expectations, and stay organized, they’re seen as reliable and capable professionals.
This kind of performance not only boosts morale but also increases visibility, opening doors to promotions, leadership opportunities, and long-term career advancement.
9. Benefits for teams and businesses
When time management becomes a team-wide practice, the impact scales beyond individual performance. Time-managed teams operate more efficiently, avoid duplication of effort, and stay aligned on priorities—resulting in smoother workflows and faster project turnaround.
From a business perspective, this translates to cost-effective operations. With clearer timelines and better coordination, organizations reduce unnecessary overtime, minimize bottlenecks, and allocate resources more strategically. The result? Higher team morale, improved productivity, and sustainable business growth.

Key strategies for time management at workplace
Mastering time management starts with small, intentional changes. Here are a few actionable strategies to help individuals and teams take control of their time:
- Use calendars and planners: Schedule tasks, set deadlines, and visualize your week to stay organized and proactive rather than reactive.
- Practice time-blocking: Dedicate specific blocks of time to focused work, meetings, and breaks. This reduces multitasking and boosts concentration.
- Try the Eisenhower matrix: Prioritize tasks by urgency and importance. This tool helps you focus on what truly matters and avoid spending time on low-impact activities.
- Limit distractions: Silence notifications, set boundaries for digital communication, and create distraction-free zones to protect your most productive hours.
Frequently asked questions (FAQs)
Conclusion
In today’s demanding work environment, time management is not optional—it is essential. From boosting productivity and job satisfaction to reducing stress and driving organizational success, the ability to manage time well is one of the most valuable skills any professional can develop.
Ready to take your next step?
Take a moment to audit how you currently spend your time. Identify one time management strategy—whether it is time-blocking, using a planner, or prioritizing with the Eisenhower Matrix—and commit to practicing it this week. Small changes can unlock powerful results.
Start improving your team’s time management today with Veris—the platform that enhances collaboration, productivity, and employee well-being.
May 28, 2025
Read time: Loading...
In recent years, the workplace has evolved significantly, with technology playing an integral role in transforming how employees work and interact within their environment. As we move into 2025, the technologies shaping employee experiences are not just about enhancing productivity; they are about improving employee well-being, collaboration, and engagement. The New Era of Physical Workplaces report by Veris delves into the technologies driving these changes, providing deep insights into the future of workspaces.
In this blog, we will explore the key technologies that are set to revolutionize employee experiences in 2025.
1. Smart workplace technology: The backbone of a connected environment
In 2025, the concept of a smart workplace will no longer be a futuristic idea but a common reality. Smart workplace technology refers to the integration of IoT (Internet of Things) devices, AI, and data analytics to create an interconnected, responsive workspace. These technologies empower businesses to provie employees with an adaptive environment, improving both efficiency and satisfaction.

Key components of smart workplaces:
- IoT-enabled devices: Sensors that monitor occupancy, air quality, and lighting, automatically adjusting conditions to optimize comfort and energy efficiency.
- AI-driven solutions: Artificial intelligence will manage resources such as meeting rooms, heating, cooling, and lighting based on real-time data, contributing to a seamless employee experience.
Why it Matters: These technologies are designed to foster a more comfortable, productive, and secure workspace. Employees will experience a workspace that intuitively adjusts to their needs, allowing them to focus on their work without the distractions of a disorganized or inefficient environment.
2. AI and automation: Streamlining processes for efficiency and engagement
AI and automation are reshaping how tasks are completed in the workplace, allowing employees to focus on strategic and value-driven activities. From automating mundane tasks to offering personalized experiences, AI and automation improve workplace efficiency, reduce stress, and empower employees to thrive.
- AI-powered personalization: AI will increasingly personalize the work environment, tailoring everything from lighting preferences to meeting room bookings based on individual user data. Imagine entering your office and the lighting adjusts to your preferred level, your workspace is set up, and your calendar is automatically populated with meetings and tasks for the day.
- Automation in administrative tasks: Routine administrative tasks, such as scheduling, attendance tracking, and resource allocation, can be automated, allowing employees to focus on higher-priority tasks. AI-based tools will analyze workflows and identify areas for optimization, ensuring smoother operations and less time spent on manual work.
Why it Matters: By automating routine processes, AI and automation free up time for employees to focus on tasks that require creativity, collaboration, and critical thinking, making work more fulfilling and less tedious.
3. Hybrid work technology: Enabling seamless collaboration anywhere
The hybrid work model is now a standard practice in many organizations, and technology is the key to making it work effectively. As businesses transition to a blend of in-office and remote work, hybrid work technology is helping bridge the gap between employees, regardless of their location.

Collaborative tools for hybrid work model:
- Cloud-based platforms: Tools like Microsoft Teams, Slack, and Zoom allow employees to communicate and collaborate effortlessly, no matter where they are working from. These platforms have become the digital office spaces where ideas are shared, meetings are held, and teamwork thrives.
- Virtual and augmented reality (VR/AR): VR and AR tools are helping create immersive meeting experiences, enabling employees to feel more connected and engaged during virtual meetings.Why it Matters: Hybrid work technologies create an inclusive work environment, allowing employees to collaborate and interact seamlessly, no matter their location. These tools not only facilitate communication but also enhance creativity, teamwork, and employee engagement.
4. Technology for employee well-being: Enhancing mental and physical health
Employee well-being has emerged as a key focus in the modern workplace. Technologies designed to enhance well-being are becoming integral to creating a healthier and more supportive work environment. From wellness apps to ergonomic furniture, technology is now being used to support employees’ mental and physical health.

- Technology-driven well-being solutions: Health-monitoring wearables, like fitness trackers, help employees keep track of vital metrics such as heart rate, sleep cycles, and physical activity, offering personalized insights into their well-being. These devices can provide employees with insights into their health and suggest personalized wellness activities.
- AI-based mental health tools: AI-driven apps provide mental health support by offering meditation exercises, stress management techniques, and virtual counseling sessions.
Why it matters: Well-being technology promotes a healthier, more balanced workforce. By offering employees the tools to monitor and improve their health, businesses can reduce burnout, improve job satisfaction, and foster a supportive environment that helps employees thrive both personally and professionally.
5. Security and privacy technology: Protecting the digital workplace
- Biometric authentication: More workplaces will adopt biometric authentication (fingerprint or facial recognition) to secure devices, apps, and office entry systems.
- AI powered threat detection: AI will be used to monitor networks for potential security threats, allowing businesses to respond quickly to cyberattacks and minimize risk.
Why it Matters: With more data being shared and stored online, ensuring privacy and security is vital for maintaining trust and preventing security breaches. By adopting the latest security technologies, businesses can protect their employees and data while maintaining compliance with privacy regulations.
6. Sustainability and green technology: Building eco-friendly workspaces
Sustainability has become a key priority in many workplaces, with technology playing a crucial role in reducing environmental impact. Green technologies are helping businesses reduce their carbon footprint and create energy-efficient work environments that align with employees’ values.
- Sustainable technologies in the workplace: Smart lighting and HVAC systems equipped with IoT sensors optimize energy consumption by adjusting the lighting and climate based on real-time occupancy and environmental factors, helping businesses minimize energy waste and improve overall efficiency.
Why it Matters: Eco-friendly workspaces contribute to a sustainable future, making employees feel good about where they work. Green technology also helps businesses save on energy costs and attract environmentally-conscious talent.
Conclusion: The future of employee experience is here!
The technologies transforming employee experiences in 2025 are not just about making work more efficient; they are about creating work environments where employees can thrive—mentally, physically, and professionally. By embracing AI, IoT, hybrid work tools, wellness technologies, and sustainable solutions, businesses are paving the way for a more connected, supportive, and fulfilling workplace experience.
As we move further into the The New Era of Physical Workplaces, these technologies will continue to evolve, providing businesses with the tools they need to enhance employee satisfaction, improve performance, and stay ahead in a rapidly changing world. To learn more about how these technologies are reshaping the workplace, download the full Veris report on The New Era of Physical Workplaces.
Discover how technology is shaping the future of work
The workplace is evolving rapidly, and staying ahead of the latest trends can give your business a competitive edge. Want to know how smart workplace technologies, AI, wellness solutions, and more are transforming employee experiences in 2025?
Download our comprehensive report to explore the cutting-edge technologies that are not only boosting productivity but enhancing overall employee well-being and engagement.
Mar 18, 2025
Read time: Loading...
In today’s fast-paced healthcare environment, hospitals face the dual challenge of ensuring robust security while maintaining a seamless patient and visitor experience. A Visitor management system (VMS) is no longer a luxury but a necessity for modern hospitals.
This blog explores the key features and benefits of a visitor management system tailored for hospitals, helping you understand why it’s a critical investment for healthcare facilities in the US, India, and beyond.
What is a visitor management system for hospitals?
A visitor management system is a digital solution designed to streamline the check-in process, track visitor activity, and enhance security within a hospital. Unlike traditional paper-based logbooks, a VMS automates the entire process, making it faster, more efficient, and secure. For hospitals, this system ensures that only authorized individuals gain access to sensitive areas while maintaining a welcoming environment for patients and their families.
Why do hospitals need a visitor management system?
Hospitals are high-traffic environments with a constant flow of patients, visitors, staff, and vendors. Without a proper system in place, managing this influx can lead to:

A visitor management system addresses these challenges, providing hospitals with a secure, efficient, and compliant way to manage visitors.
10 key features to look in a visitor management system for hospitals
When choosing a VMS for hospitals, look for the following features to ensure it meets your facility’s unique needs:
1. Touchless check-in
- With the rise of health concerns, touchless check-in options like QR codes or facial recognition minimize physical contact and reduce the risk of spreading infections.
2. Real-time visitor tracking
- Track the movement of visitors in real-time, ensuring they only access authorized areas. This feature is crucial for maintaining security in sensitive zones like ICUs and operating rooms.
3. Pre-registration and appointment scheduling
- Allow visitors to pre-register online, reducing wait times and ensuring a smooth check-in process. This is especially useful for outpatient departments and scheduled visits.
4. ID verification and badge printing
- Automatically verify visitor IDs and print customized badges with visitor details, photo, and access permissions. This enhances accountability and security.
5. Integration with access control systems
- Seamlessly integrate the VMS with existing access control systems to restrict entry to restricted areas and ensure only authorized personnel gain access.
6. Emergency alerts and notifications
- Send instant alerts to security personnel in case of unauthorized access or emergencies, ensuring a quick response to potential threats.
7. Compliance and reporting
- Generate detailed visitor logs and reports to meet regulatory requirements and maintain audit trails for security purposes.
8. Visitor health screening
- Include health screening questions (e.g., fever, recent travel) during the check-in process to ensure the safety of patients and staff.
9. Multi-language support
- For hospitals in diverse regions like India, multi-language support ensures that visitors can easily navigate the check-in process.
10. Cloud-based storage
- Store visitor data securely in the cloud, ensuring easy access and retrieval while maintaining data privacy.
What are the benefits of a visitor management system for hospitals
Implementing a VMS in hospitals offers numerous benefits, including:
1. Enhanced security
- Prevent unauthorized access to restricted areas and ensure only approved visitors enter the premises. Real-time tracking and ID verification add an extra layer of security.
2. Improved patient and visitor experience
- Reduce wait times and streamline the check-in process, creating a positive experience for patients and their families.
3. Efficient staff workflow
- Automating visitor management frees up staff to focus on critical tasks, improving overall operational efficiency.
4. Health and safety compliance
- With features like health screening and touchless check-in, hospitals can maintain a safe environment for patients, visitors, and staff.
5. Regulatory compliance
- Maintain accurate visitor logs and generate reports to meet healthcare regulations and standards.
6. Scalability
- Whether it’s a small clinic or a large multi-specialty hospital, a VMS can scale to meet the needs of any healthcare facility.
7. Data-driven decision making
- Analyze visitor data to identify trends, optimize processes, and improve resource allocation.
Visitor management systems in hospitals-Used cases

Conclusion
A visitor management system is an indispensable tool for hospitals looking to enhance security, streamline operations, and improve the overall patient and visitor experience. With features like touchless check-in, real-time tracking, and health screening, a VMS ensures that hospitals can maintain a safe and efficient environment while meeting regulatory requirements.
Whether you’re managing a large multi-specialty hospital in the US or a small clinic in India, investing in a robust visitor management system is a step toward a safer, more organized, and patient-centric healthcare facility.
Ready to transform your hospital’s visitor management?
Explore our cloud-based visitor management system designed specifically for healthcare facilities. Request a free demo today and see how we can help you enhance security and efficiency!
Mar 5, 2025
Read time: Loading...
In today’s fast-paced world, security and convenience are no longer mutually exclusive. With the rise of smart technology, mobile access control systems are revolutionizing how gated communities and co-working spaces manage security. Gone are the days of lost key cards or forgotten PINs. Instead, smartphones are becoming the ultimate tool for seamless, secure, and scalable access control.
But what makes mobile access control systems a game-changer for these spaces? Let’s dive into the benefits, features, and reasons why this technology is transforming security for gated communities and co-working spaces globally.
What is a mobile access control system?
A mobile access control system is a modern security solution that uses smartphones as digital keys. Instead of relying on traditional methods like physical keys, key cards, or fobs, users can unlock doors, gates, or elevators using their mobile devices. These systems leverage technologies like Bluetooth, NFC (Near Field Communication), and cloud-based platforms to provide secure, touchless, and convenient access.
Why do gated communities need mobile access control systems?
Gated communities are designed to offer residents a safe and secure living environment. However, traditional access control methods often fall short in meeting modern security demands.

1. Enhanced security
- Eliminates key duplication: Physical keys or cards can be duplicated, posing a security risk. Mobile credentials are encrypted and unique to each user, making them nearly impossible to replicate.
- Real-time monitoring: Property managers can track who enters or exits the community in real-time, ensuring only authorized individuals gain access.
- Remote access management: Grant or revoke access remotely, even if you’re not on-site. This is especially useful for visitors, delivery personnel, or service providers.
2. Convenience for residents
- No more lost keys: Residents no longer need to worry about losing key cards or fobs. Their smartphone is always with them, acting as a digital key.
- Touchless entry: In a post-pandemic world, touchless access is a significant advantage. Residents can unlock gates or doors without touching shared surfaces.
- Visitor management: Residents can grant temporary access to guests or service providers directly from their phones, eliminating the need for manual intervention.
3. Scalability
- Mobile access control systems are highly scalable, making them ideal for large gated communities with hundreds of residents. Adding new users or updating access permissions is quick and hassle-free.
How do co-working spaces benefit from mobile access control
Co-working spaces are dynamic environments with a constant flow of members, guests, and visitors. Traditional access control methods can be cumbersome and inefficient in such settings. Here’s how mobile access control systems are transforming co-working spaces:
1. Streamlined access for members
- 24/7 access: Members can access the co-working space at any time using their smartphones, even outside business hours.
- Multi-location access: For co-working spaces with multiple locations, mobile access control allows members to seamlessly access all facilities with a single digital credential.
2. Improved visitor management
- Temporary access: Co-working space managers can issue temporary access credentials to guests or clients, which expire automatically after a set time.
- Integration with booking systems: Mobile access control can integrate with booking or scheduling software, ensuring only registered users can enter during their allotted time.
3. Enhanced security
- Audit trails: Maintain detailed logs of who accessed the space and when. This is crucial for security and compliance purposes.
- Instant alerts: Receive instant notifications if unauthorized access is attempted.
4. Cost-effective and future-Proof
- No hardware costs: Unlike traditional systems that require key cards or fobs, mobile access control eliminates the need for physical credentials, reducing long-term costs.
- Easy updates: Software updates can be rolled out remotely, ensuring the system stays up-to-date with the latest security features.
What are the key features of mobile access control systems

Mobile access control: A growing trend
The demand for mobile access control is driven by the need for touchless solutions and smart building integration. Gated communities and co-working spaces are increasingly adopting this technology to enhance security and convenience. Rapid urbanization and the rise of smart cities are also fueling the adoption of mobile access control systems in urban areas worldwide.
Conclusion
Mobile access control systems are no longer a luxury—they are a necessity for gated communities and co-working spaces looking to enhance security, convenience, and scalability. By replacing outdated methods with smartphone-based solutions, these spaces can offer a seamless and secure experience for residents, members, and visitors.
Whether you’re managing a gated community or a co-working space, now is the time to embrace this game-changing technology.
Ready to upgrade your security?
Contact Veris today or schedule a demo and discover how mobile access control can transform your space.
Feb 20, 2025
Read time: Loading...
In today’s digital-first world, organizations process massive volumes of personal data, from customer records and employee details to visitor information. With growing cybersecurity threats, data breaches, and unauthorized data sharing, governments worldwide are tightening regulations to protect personal information.
India has introduced the Digital Personal Data Protection (DPDP) Act, 2023 to ensure businesses and organizations responsibly handle personal data. This law mandates transparency, user consent, and strict data security protocols, placing greater accountability on CXOs, administrators, and security professionals.
For businesses, understanding DPDP is about legal compliance, protecting brand reputation, maintaining customer trust, and ensuring smooth business operations. This guide breaks down what DPDP entails, its key provisions, why businesses should take it seriously, and how workplace solutions can help organizations remain compliant.
What is the DPDP Law?
The Digital Personal Data Protection (DPDP) Act, 2023 is India’s first comprehensive data privacy law, modeled after global regulations like the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA).
This act governs how organizations collect, store, and process personal data while ensuring individuals have control over their personal information. It aims to safeguard the rights of data owners while setting strict obligations for data handlers.
Who does the DPDP act apply to?
- Any business operating in India that collects, processes, or stores personal data of individuals.
- Organizations outside India that process Indian users’ data.
- Public and private entities that handle sensitive information, including visitor records, employee details, and customer databases.
Failing to comply with the DPDP Act can lead to heavy fines, legal action, and reputational damage.
What are the key highlights of the DPDP Act
The DPDP Act introduces several critical regulations that impact businesses across industries. Here are some key aspects:

Why should workplaces care?
For the workplaces DPDP Act is a business necessity. Here’s why:
✅ Avoid heavy fines & legal risks: Businesses that fail to comply with DPDP can face substantial financial penalties, harming revenue and long-term sustainability.
✅ Build customer & employee trust: In an era where data breaches make headlines, ensuring data privacy strengthens brand reputation and employee confidence.
✅ Prevent cybersecurity threats: Data breaches can cost millions in damages and lost revenue. A DPDP-compliant system minimizes the risk of cyberattacks and unauthorized access.
✅ Competitive advantage: Organizations that prioritize data security gain a strategic edge, showing stakeholders and customers that they prioritize privacy.
✅ Operational efficiency: A structured data compliance system reduces manual errors, strengthens governance, and enhances workplace security.
How to ensure your workplace adheres to DPDP law?
1. Implement a strong data protection framework
- Establish secure data storage and encryption policies.
- Limit who has access to sensitive personal data.
- Conduct regular cybersecurity audits.
2. Use secure digital workplace solutions
- Adopt visitor & workplace management systems that securely handle visitor and employee data.
- Ensure access control systems allow only authorized personnel into secure zones.
3. Conduct compliance audits & employee training
- Train employees on data protection best practices.
- Regularly audit workplace security protocols.
4. Ensure third-party data compliance
- Review data handling policies of vendors and third-party service providers.
- Work with DPDP-compliant partners to maintain secure data exchanges.
5. Prepare for data breach incidents
- Develop a data breach response strategy.
- Enable real-time alerts for unauthorized data access.
What is the role of smart workplace solutions in data protection?
A visitor management system (VMS) and access control solutions play a crucial role in maintaining compliance with the DPDP Act. Here’s how:

By leveraging smart workplace solutions, organizations can seamlessly comply with DPDP regulations while improving efficiency, security, and user experience.
The DPDP Act is transforming how businesses handle personal data. Compliance is essential for avoiding penalties, building trust, improving security, and driving operational efficiency.
With smart workplace solutions, businesses can:
✅ Streamline visitor & employee data management
✅ Ensure regulatory compliance with automated security protocols
✅ Prevent data breaches and unauthorized access
Is your workplace DPDP-compliant?
Ensure data security and compliance with Veris. Schedule a free demo today!
Feb 17, 2025
Read time: Loading...
Compliance is a fundamental requirement for businesses, ensuring ethical operations and adherence to regulatory standards. Organizations must implement secure processes that safeguard data and control access for employees and third parties while aligning with evolving legal frameworks.
Compliance management goes beyond basic adherence—it involves systematically evaluating regulations, implementing controls, and continuously monitoring processes to mitigate risks. As cyber threats evolve, businesses must remain agile in adjusting their security protocols to meet new requirements such as GDPR, HIPAA, and other international, national, and industry-specific regulations.
What is compliance management?
Compliance management refers to the structured approach organizations take to ensure alignment with industry regulations and security policies. This process includes identifying relevant legal frameworks, assessing current security measures, implementing necessary controls, and conducting regular monitoring and reporting.
The goal is not just to meet minimum standards but to build a resilient system that safeguards sensitive data, maintains customer trust, and minimizes security risks. Effective compliance management involves developing policies that govern data usage, enforcing strict access control measures, and fostering a security-conscious culture through employee training and continuous auditing.
In today’s digital landscape, traditional compliance efforts are insufficient. Businesses must proactively adapt to regulatory updates, ensuring they stay compliant while avoiding penalties and reinforcing security best practices.
Why is compliance management essential?
Historically, some organizations opted to pay fines instead of investing in compliance measures. However, with increasingly strict regulations and rising penalties, non-compliance is no longer a viable option. Regulatory bodies, including GDPR, HIPAA, SOX, and CCPA, impose significant fines on businesses that fail to protect sensitive data.
For instance, GDPR violations have led to multi-million-dollar penalties for major corporations. British Airways was fined £183 million for a security breach that compromised customer data. Such incidents highlight the financial and reputational risks of non-compliance.
With stringent laws at both state and federal levels, businesses must adopt comprehensive compliance management strategies. Failure to comply can lead to legal consequences, operational disruptions, and damage to customer trust.
Key compliance frameworks
- General Data Protection Regulation (GDPR) – Protects the personal data of EU citizens.
- Health Insurance Portability and Accountability Act (HIPAA) – Regulates healthcare data in the U.S.
- ISO/IEC 27001 – International standard for information security management.
- Digital Personal Data Protection (DPDP) Act – India’s comprehensive data protection law that mandates how organizations handle and secure personal data. Read more about how the DPDP act impact business and workplace security.
Examples of compliance management in action
A robust compliance strategy safeguards an organization’s digital assets and enhances operational security. Here’s how compliance management supports different industries:

By integrating compliance management into daily operations, companies not only mitigate risks but also improve overall security and data governance.
What are the key steps in a compliance management program?
A well-structured compliance program follows a systematic process to ensure regulatory adherence and operational efficiency.
- Identifying compliance requirements: Businesses must review applicable laws, including industry-specific standards like ISO/IEC 27001 and NIST frameworks.
- Assessing current security measures: Conducting audits and risk assessments helps identify compliance gaps and vulnerabilities.
- Developing policies and procedures: Organizations must establish clear guidelines on data protection, user access, and cybersecurity best practices.
- Implementing security controls: This includes deploying encryption, access control mechanisms, and incident response plans to safeguard sensitive information.
- Training employees: Ensuring staff members understand compliance policies through regular training sessions is essential for maintaining a secure environment.
- Ongoing monitoring and auditing: Continuous tracking of compliance status, system vulnerabilities, and policy adherence ensures sustained security and regulatory alignment.
What are the challenges in compliance management?
Despite its importance, businesses face multiple challenges in maintaining compliance:
- Regulatory complexity: Keeping up with evolving global, national, and industry-specific regulations requires ongoing vigilance.
- Frequent policy updates: Compliance laws change regularly, necessitating continuous adaptation of security measures.
- Integration with existing systems: Ensuring compliance across diverse IT infrastructures can be challenging.
- Cross-departmental coordination: Aligning compliance policies across multiple teams requires effective communication and collaboration.
- Resource allocation: Organizations must invest in tools, training, and personnel to manage compliance effectively.
Addressing these challenges requires a proactive approach that blends technological advancements, employee awareness, and strategic governance.
How a visitor management system ensures compliance?
A visitor management system (VMS) is more than just access control—it’s a compliance enabler. It streamlines visitor tracking, ensures security, and simplifies regulatory adherence.
- Customized check-ins for compliance
A VMS tailors check-in processes for different visitor types:
- Contractors submit safety certifications.
- Vendors sign NDAs.
- Guests acknowledge policies. This ensures businesses meet industry regulations effortlessly.
- Digital visitor logs for audits
Automatic check-in/out logs provide a complete record of visitor activity, simplifying audits and ensuring compliance.
- Emergency notifications for workplace safety
With laws like California’s SB 553, real-time alerts are essential. A VMS sends emergency notifications to employees and visitors, improving safety and compliance.
- Access control integration
A VMS integrates with access control to manage permissions efficiently:
- Labs restrict access to authorized personnel.
- Admin teams access only common areas.
- Contractors receive temporary, role-based access. This reduces unauthorized entry and enhances security.
- Automated data security
By tracking visitor data and controlling access, a VMS minimizes risks and improves compliance through automation. Investing in a VMS ensures regulatory compliance, workplace security, and operational efficiency.
Ensure compliance with Veris!
Upgrade your visitor management with Veris and stay audit-ready. Schedule a demo today!
Feb 6, 2025
Read time: Loading...
Creating a personalized visitor experience makes guests feel valued and welcomed in your workplace. Whether it’s a potential hire, a business partner, or a contractor, tailoring their experience ensures they leave with a great impression of your company. People appreciate personal touches more than generic interactions.
Not every visitor is the same. You wouldn’t welcome a job candidate the same way you would greet a vendor. A candidate may appreciate a warm greeting and an office tour, while a vendor may need seamless access to supply rooms.
But the visitor experience doesn’t begin when they step through the door—it starts with the invitation. A visitor management system (VMS) is a game-changer, ensuring a smooth, customized journey for every visitor. Let’s explore five common visitor types and how to make their experience exceptional.

1. Business partners
Your business partners—clients, investors, or prospects—play a crucial role in your company's success. Their visit should reflect professionalism and efficiency.
How to impress them:
- Use instant host notifications to ensure a warm and timely welcome.
- Enable digital pre-registration so legal paperwork can be signed in advance.
- Offer a seamless check-in experience using Veris visitor management with QR code-based entry, eliminating long wait times.
- Provide a designated meeting space, complete with refreshments and key presentation materials.
A frictionless experience builds trust, strengthens relationships, and leaves a lasting positive impression of your brand.
2. Job candidates
Interviews can be nerve-wracking. Ensuring a seamless candidate experience can make a difference in their perception of your company.
How to impress them:
- Send a detailed invite email with information about the location, meeting time, and whom they will meet.
- Use Veris visitor pre-check-in to allow candidates to complete paperwork in advance.
- Provide a visitor badge and printed schedule upon arrival, ensuring they feel prepared and confident.
- Offer a guided office tour to showcase your company culture and work environment.
A well-organized, warm welcome enhances the candidate experience and increases the chances of securing top talent.
3. Contractors & freelancers
Contractors and freelancers contribute significantly to business operations. Making their visit smooth allows them to focus on delivering results.
How to impress them:
- Allow pre-registration and automated check-in for returning contractors.
- Assign a hot desk using Veris’ integrated workspace management system.
- Enable Wi-Fi access automation, ensuring seamless connectivity upon check-in.
- Grant temporary access credentials to restricted areas if necessary.
A well-managed experience ensures that external talent can collaborate effortlessly with your teams.
4. Food & supply vendors
Your workplace runs efficiently thanks to vendors who restock supplies and cater to your employees. Ensuring their experience is hassle-free keeps operations smooth.
How to impress them:
- Use a visitor management system that integrates with access control to provide secure, temporary access.
- Assign access levels so vendors can only enter designated areas such as supply rooms or storage spaces.
- Automate check-in and check-out to minimize disruptions while keeping track of vendor activity.
A streamlined process allows vendors to do their jobs efficiently without affecting workplace productivity.
5. Friends & family visitors
Sometimes employees invite family or friends for lunch, a quick tour, or office events. Ensuring a simple and secure check-in process enhances the experience for everyone.
How to impress them:
- Use ID verification to ensure compliance with visitor policies.
- Allow pre-registration to track the number of expected guests.
- Assign designated seating areas or meeting spots for a smooth visit.
With a streamlined system in place, hosting personal guests becomes effortless while maintaining workplace security.
Make every visitor’s experience exceptional
Regardless of the visitor type, a well-planned visitor management process ensures efficiency, security, and a welcoming atmosphere. While a VMS takes care of check-ins and compliance, it’s the personal touches—a friendly greeting, a seamless process, and an intuitive experience—that make all the difference.
Ready to enhance your workplace visitor experience? Schedule a demo with Veris today and discover how our visitor management solutions can create a seamless and secure check-in journey for every guest!
Feb 6, 2025
Read time: Loading...
In today’s rapidly evolving workplace, businesses are reimagining office environments to be more intelligent, connected, and efficient. The concept of smart spaces is transforming traditional workplaces into dynamic ecosystems that optimize resources, enhance employee experiences, and improve operational efficiency. But what exactly are smart spaces, and why should businesses invest in them? Let’s explore.
What are smart spaces?
A smart space is a technology-driven environment that uses IoT sensors, AI, and automation to create an adaptive and data-informed workplace. These spaces leverage real-time analytics to monitor space utilization, energy consumption, employee movement, and security—leading to better decision-making and an optimized work environment.
By integrating cloud-based workplace solutions, occupancy sensors, and AI-driven analytics, businesses can ensure that their offices are not just places to work but strategic assets that drive productivity and efficiency.
What are top 5 smart spaces examples in action?
Smart spaces are being implemented across various industries to enhance operational efficiency and user experience. Here are some real-world examples:
- Corporate offices – Leading companies use IoT sensors and AI-driven analytics to optimize office layouts, manage meeting room bookings, and automate lighting and climate control for energy savings.
- Hotels & hospitality – Smart hotel rooms use voice-activated assistants, automated lighting, and climate control to provide personalized guest experiences.
- Healthcare facilities – Hospitals leverage smart space technology for real-time patient monitoring, asset tracking, and improved workflow automation, ensuring better patient care.
- Retail stores – Smart retail spaces use digital signage, AI-driven customer analytics, and automated inventory management to enhance shopping experiences and streamline operations.
- Educational institutions – Universities utilize smart classroom technology, facial recognition for attendance tracking, and automated HVAC controls to improve learning environments and energy efficiency.
Why are smart spaces important for business ?
The shift to hybrid work models has emphasized the need for flexibility and adaptability in office spaces. Here’s how smart spaces address these challenges:
✅ Optimized space utilization – Smart sensors track real-time occupancy, ensuring office layouts are designed for maximum efficiency. Businesses can identify underutilized areas and repurpose them for better use.
✅ Enhanced employee experience – A smart office offers seamless desk booking, meeting room reservations, and wayfinding, allowing employees to navigate their work environment with ease.
✅ Energy efficiency & sustainability – Automated lighting, climate control, and occupancy-based power usage help businesses reduce energy costs and achieve sustainability goals.
✅ Improved workplace security – Smart access control systems restrict unauthorized entry, while real-time monitoring ensures a safer and more secure work environment.
✅ Data-driven decision making – Workplace analytics provide insights into employee work patterns, helping leadership make informed decisions about space allocation and resource planning.
What are key smart space technologies?

How can businesses implement smart spaces?
To transition into a smart workplace, companies should:
- Evaluate current workplace needs – Identify inefficiencies and areas for improvement.
- Invest in the right technology – Choose IoT-driven workplace solutions that align with business goals.
- Enable seamless integration – Ensure all systems, from visitor management to access control, work together.
- Train employees on smart solutions – Encourage employees to leverage smart tools for productivity and efficiency.
- Continuously monitor and optimize – Use real-time data and AI analytics to improve the workspace continually.
What is the future of smart spaces?
As businesses continue to adapt to changing work dynamics, smart spaces will play a critical role in ensuring agility, efficiency, and employee satisfaction. The integration of AI, IoT, and cloud-based workplace solutions will not only drive operational improvements but also create work environments that foster innovation and collaboration.
Are you ready to build a smart workplace? Transform your office into a data-driven, intelligent space with Veris.
Schedule a demo today and discover how our smart workplace solutions can help you create a more connected and productive workspace!
Jan 30, 2025
Read time: Loading...
In our previous blog, workplace analytics and why you need it, you learned about workplace analytics, its benefits, and what to consider when selecting a workplace analytics software. If you missed it or need a quick recap, now’s the time to catch up!
In this blog, on workplace analytics we’re diving deeper. Here we will cover:
- What space optimization means
- The hidden costs of inefficient office space
- 3 ways to leverage workplace analytics for better space utilization
What is space optimization?
Space optimization is the process of ensuring every workspace is used effectively. By utilizing real-time data from workplace analytics, businesses can make informed decisions that reduce costs and enhance employee experiences.
How inefficient office space impacts your organization
Understanding why space optimization matters can help build a strong business case for investing in the right tools. Let’s explore the hidden costs of underutilized or mismanaged workspace.

3 ways to use workplace analytics for space optimization
Now that we’ve covered why inefficient space is a problem, let’s explore how analytics can help businesses maximize space utilization and improve workplace experiences.
1. Monitor return-to-office (RTO) trends
A workplace analytics platform helps track occupancy and attendance patterns, allowing businesses to analyze when and how employees use the office. Breaking this data down by individuals, teams, and departments provides actionable insights that can shape return-to-office policies and improve space planning.
For instance, if certain teams frequent the office on specific days, workspace configurations can be adjusted to accommodate their needs, ensuring they have access to the right areas, equipment, and staffing support.
If your organization has a hybrid work policy, analytics can help measure compliance and identify gaps in attendance.
2. Plan for shifts in workplace foot traffic
A robust workplace analytics system provides accurate headcounts, helping businesses better manage space, staffing, and amenities. It accounts for both registered and walk-in employees and visitors, offering a clearer picture than traditional badge access data alone.
With this data, businesses can:
- Optimize staffing levels: If midweek sees peak occupancy, more staff can be scheduled to manage front-desk operations and services.
- Improve event planning: If an onsite event is scheduled, knowing expected attendance helps in selecting the right venue and arranging necessary resources without disrupting others.
- Schedule maintenance efficiently: Broken office equipment or meeting room tech can disrupt workflow. By planning maintenance on low-occupancy days, disruptions can be minimized. Additionally, smart room scheduling systems can automatically reroute employees to alternative spaces when repairs are in progress.
3. Foster a more flexible workplace
Workplace analytics provides insights into how different spaces are used—whether it’s meeting rooms, bookable desks, work pods, or collaborative areas. By analyzing these usage patterns, businesses can create a more dynamic and responsive workspace.
For example:
- On quiet days, employees might prefer individual desks or private focus areas for deep work.
- On busier days, demand for collaborative meeting spaces may rise as teams gather for brainstorming sessions.
By leveraging data-driven insights, businesses can reconfigure layouts, add needed amenities, and adjust space availability throughout the week to better meet employee needs. This ensures that no matter when an employee comes in, they find a productive, comfortable, and well-equipped environment.
By using workplace analytics, businesses can make data-backed decisions that enhance efficiency, cut costs, and create a more engaging employee experience. Investing in the right analytics tools ensures that workspace planning evolves alongside employee needs, leading to smarter, more adaptable workplaces.
In short, inefficient space drains resources—it drives up costs, hampers productivity, and diminishes the onsite experience. By optimizing your workplace, you ensure employees can make the most of every space, creating a win-win for your team, your workforce, and your bottom line.
Want to take your workplace optimization to the next level? Start leveraging a real-time workplace analytics platform today!
Jan 30, 2025
Read time: Loading...
A recent study found that over half (53%) of organizations lack the necessary workplace data to make strategic decisions. If you’re a workplace manager without access to actionable insights, it’s like planning a journey without knowing your starting point.
To optimize your workspace effectively, you need clarity on key factors: How many employees are utilizing the space? When are they coming in? What are their work preferences? Where are opportunities for improvement? Tracking these critical metrics is essential for both operational efficiency and creating a workplace that employees genuinely enjoy.
In this blog, we’ll introduce you to the fundamentals of workplace analytics and guide you on how to get started. We’ll explore:
- What is workplace analytics is and why it matters
- Key examples of workplace analytics
- 4 essential questions to ask when selecting workplace analytics software
What is workplace analytics
Workplace analytics refers to a set of tools and dashboards designed to track key data points such as space utilization, employee attendance, and visitor volume. These insights empower businesses to make strategic, cost-effective decisions that optimize workplace management. For instance, organizations can assess real estate needs, refine staffing strategies, and enhance the overall employee experience.
However, not all workplace analytics solutions offer the same value. Some platforms provide raw data without actionable insights, leaving businesses with more questions than answers. The most effective solutions go beyond mere numbers, identifying meaningful trends and providing recommendations that help decision-makers take confident, informed actions.
The benefits of workplace analytics
If you’re wondering whether another workplace management tool is necessary, the answer is a resounding yes. The advantage of workplace analytics is that it simplifies decision-making. By using a unified workplace platform that integrates seamlessly with your existing systems, you gain a comprehensive view of space utilization and employee behavior, unlocking a range of benefits.

3 key metrics of workplace analytics
Now that we’ve covered the benefits, let’s explore the specific workplace metrics you can track with the right analytics tools.
Attendance Trends
Tracking attendance patterns provides valuable insight into workforce behavior, helping businesses manage space effectively.

Space Utilization
Space utilization data assesses how effectively desks, meeting rooms, and shared spaces are being used. It tracks desk occupancy rates, room booking efficiency, and usage trends for common areas.

Benchmarking against industry standards
Advanced workplace analytics platforms enable businesses to compare their space utilization and attendance trends against industry peers.

Choosing the right workplace analytics software: 4 key questions
Now that you understand workplace analytics, how do you choose the best solution for your business? Here are four critical questions to ask:
1. Do you need a point solution or a comprehensive workplace platform?
While standalone tools may solve one immediate need (like meeting room booking), a comprehensive platform offers long-term value. A unified workplace platform not only helps with space reservations but also provides insights on attendance, space optimization, and operational efficiency—all in one place.
2. Will the software scale with your business?
Your workplace needs today may be different from what you’ll need in the future. Choose an analytics solution that scales across multiple locations and can adapt to business growth.
3. Does the software integrate with third-party applications?
Seamless integration with tools like access control systems, Wi-Fi tracking, and security solutions enhances workplace efficiency. The fewer manual processes involved, the smoother the experience for employees and IT teams alike.
4. Is the software user-friendly?
Adoption is key. The best workplace analytics solutions are intuitive and easy to use, ensuring employees engage with them regularly. The more they interact with the system, the more accurate and actionable the insights become.
Workplace analytics is more than just data—it’s about unlocking the full potential of your workspace. By investing in the right workplace analytics platform, you can make informed decisions, improve operational efficiency, and create a workplace that employees love. Whether you’re looking to optimize meeting room bookings, enhance security, or boost productivity, workplace analytics provides the insights you need to succeed.
Are you ready to take control of your workplace data? Explore how Veris can help you turn insights into action.
Jan 28, 2025
Read time: Loading...
Visitor screening has become an integral part of modern visitor management systems, offering enhanced security, compliance, and operational efficiency. By ensuring that only authorized individuals gain access to your premises, visitor screening helps organizations safeguard their employees, data, and physical assets. In this guide, we’ll break down the essentials of visitor screening, its benefits, and how it fits seamlessly into your overall security strategy.
What is visitor screening?
Visitor screening is the process of evaluating and verifying individuals before granting them access to your facility. This can range from capturing visitor information and running background checks to confirming adherence to organizational policies, such as vaccination or identification requirements.
A robust visitor screening process not only ensures safety but also creates a welcoming and professional experience for guests. With the right visitor management system in place, organizations can automate these checks, reducing manual effort while maintaining high-security standards.
Why is visitor screening important?
Visitor screening plays a crucial role in protecting workplaces, particularly in a time where security threats and compliance regulations are increasing. Here’s why it matters:
- Enhanced security: Screening visitors helps prevent unauthorized access, reducing the risk of theft, espionage, or workplace violence.
- Regulatory compliance: Industries like healthcare, finance, and education often require organizations to maintain strict access protocols. Visitor screening ensures compliance with regulations, such as HIPAA, GDPR, and other regional standards.
- Health and safety measures: Especially post-pandemic, health-related checks (like vaccination status or temperature scans) have become a vital part of visitor screening to protect employees and visitors alike.
- Operational efficiency: Automated visitor screening saves time by quickly verifying guest details, allowing front-desk staff to focus on other priorities.
Key elements of an effective visitor screening process
1. Pre-registration
Allow visitors to pre-register their details before arriving. This reduces wait times and provides security teams with the necessary information to evaluate guests in advance.
2. Identity verification
Require government-issued identification or other forms of authentication to confirm the visitor’s identity. This step is critical for ensuring that the individual is who they claim to be.
3. Policy acknowledgment
Organizations can ask visitors to acknowledge and agree to specific policies, such as non-disclosure agreements (NDAs) or health and safety protocols, before entering the facility.
4. Health and safety checks
Screening processes may include temperature scans, health questionnaires, or verifying vaccination records, depending on the organization’s policies.
5. Watchlist screening
Check visitors against internal or external watchlists to ensure no flagged individuals gain access to your premises. This is especially important for industries with heightened security requirements.
6. Provide visitor badge
Provide visitors with temporary visitor badges or e-badges to help staff easily identify guests and their level of access within the facility.
How technology powers visitor screening
Modern visitor screening is powered by advanced visitor management solutions, like Veris, which integrate seamlessly with existing security systems. These platforms automate the entire screening process, from pre-registration to real-time alerts, making it easier to maintain a secure environment without slowing down operations.
Key technological features of visitor screening include:


The Veris advantage in visitor screening
At Veris, we understand the importance of a seamless, secure, and efficient visitor screening process. Our visitor management platform combines advanced technology with user-friendly interfaces to create a superior experience for both organizations and their guests.
Here’s what sets Veris apart:
- Fully customizable workflows to match your specific screening requirements.
- Cloud-based systems for scalability and reliability.
- Integration capabilities with existing security and HR systems for a unified experience.
- Real-time alerts and notifications for immediate action when necessary.
Visitor screening is no longer a “nice-to-have” but a “must-have” for any organization looking to enhance security, compliance, and operational efficiency. With the right tools, like the Veris visitor management system, businesses can streamline the screening process while providing a professional and secure environment for employees and guests alike.
Make the shift to smarter visitor management today—choose Veris.
Jan 21, 2025
Read time: Loading...
Attendance management systems have become essential tools for businesses aiming to streamline their workforce operations. Whether you're managing a remote team, hybrid work model, or an on-site workforce, an efficient attendance management system can make all the difference. This guide dives deep into the essentials of these systems, covering their types, benefits, key features, and best practices to help you choose the ideal solution for your organization.
What is an attendance management system?
An attendance management system is a digital solution designed to monitor, record, and manage employee attendance, working hours, and schedules. It replaces traditional methods such as manual registers or spreadsheets, ensuring a seamless and automated experience. These systems allow managers to track attendance patterns, ensure punctuality, and gather insights to improve workforce efficiency. Advanced solutions also integrate with payroll, HR software, and project management tools, offering an all-in-one solution for modern workplaces.
Why every business needs an attendance management system
Modern workplaces are dynamic, with teams working across locations and time zones. Managing attendance manually can lead to errors, inefficiencies, and compliance challenges. Implementing an attendance management system offers:

Businesses of all sizes can benefit from adopting an online attendance management system to enhance their operational efficiency.
Types of attendance management systems
a. Online attendance management system
An online attendance management system operates through cloud platforms. Employees can log their attendance from any location, making it ideal for remote or hybrid teams.
Key Advantages:
- Accessibility from anywhere.
- Real-time synchronization of data.
- Easy integration with other workplace systems.
This system is particularly useful for companies that prioritize flexibility and remote work.
b. Employee attendance management system
The employee attendance management system focuses on tracking individual schedules and productivity. It provides a detailed overview of attendance, overtime, and leaves, helping managers optimize workflows.
Features:
- Shift scheduling and management.
- Comprehensive reports on attendance trends.
- Leave and holiday tracking for better planning.
c. Time and attendance management system
A time and attendance management system goes beyond basic tracking by incorporating time management tools. It monitors working hours, tracks productivity, and helps businesses comply with labor laws.
Best for:
- Teams with complex schedules.
- Companies needing compliance monitoring.
- Organizations focused on productivity metrics.
d. Biometric attendance management system
Biometric systems use unique physical identifiers, such as fingerprints, facial recognition, or iris scans, to record attendance.
Why choose biometrics?
- Eliminates the risk of buddy punching.
- Ensures high accuracy in attendance tracking.
- Strengthens workplace security.
Key features of a good attendance management system
To maximize the benefits, ensure your chosen system includes the following features:

Benefits of using an attendance management system
- Enhanced accuracy: Automated systems eliminate manual errors, ensuring precise data collection for payroll and compliance purposes.
- Time savings: Managers save hours previously spent on manual attendance tracking, allowing them to focus on strategic priorities.
- Boosted productivity: Transparent systems promote punctuality, fostering a culture of accountability and efficiency.
- Regulatory compliance: Advanced systems help organizations adhere to labor laws by maintaining accurate records of working hours.
- Cost efficiency: Streamlined processes and optimized workforce management reduce overhead costs, making these systems a cost-effective investment
How to choose the right attendance management system
Selecting the right attendance management system can transform your workforce management. Here’s how to choose:
Step 1: Identify your needs
Consider your team size, work model (remote, hybrid, or on-site), and specific challenges.
Step 2: Evaluate features
Look for systems with features like mobile access, real-time reporting, and integration capabilities.
Step 3: Test user experience
Ensure the system is user-friendly for both employees and administrators.
Step 4: Compare vendors
Research vendors’ reputations, customer support quality, and system scalability to find a reliable partner.
Integration capabilities of attendance systems
Modern attendance management systems integrate seamlessly with:

Such integrations not only enhance efficiency but also create a unified ecosystem for business operations.
Role of AI in attendance management systems
AI-powered solutions are reshaping the landscape of attendance management. These systems offer:

AI-driven features ensure that businesses stay ahead in managing their workforce effectively.
Overcoming challenges in attendance management
- Employee resistance: Introduce the system with proper training and emphasize its benefits, such as reduced errors and convenience.
- Data privacy concerns: Choose systems with robust security measures, such as end-to-end encryption and compliance with GDPR or similar regulations.
- Integration barriers: Partner with vendors who offer technical support and customization options to ensure smooth integration with existing systems.
Future trends in attendance management systems
The future of attendance management is exciting, with innovations like:

These trends will redefine how businesses manage their workforce in the coming years.
An attendance management system is no longer a luxury but a necessity for businesses looking to thrive in a competitive environment. Whether it’s an online attendance management system, a biometric attendance management system, or a comprehensive time and attendance management system, investing in the right solution can significantly enhance your workforce management.
Take the next step toward smarter attendance management
Ready to revolutionize how you manage attendance in your organization? Don’t let manual processes hold you back! Explore our advanced attendance management system and experience seamless, efficient, and accurate workforce tracking.
🌟 Whether you’re a small business or a large enterprise, our system is designed to scale with your needs.
📞 Contact us today or schedule a free demo or consultation and see how our smart workplace solutions can transform your workforce management.
Jan 18, 2025
Read time: Loading...
In today's fast-paced world, efficiency is key. Whether you're managing an office building, a school, or any facility with frequent visitors, a streamlined check-in process can save time, enhance security, and improve the overall experience for everyone involved.
In this article, we'll explore how technology can revolutionize visitor check-in procedures, focusing on the advantages of using a visitor management system, the best options available, and how these systems integrate with access control and visitor tracking software.
The importance of a streamlined visitor check-in process
First impressions matter, and the check-in process is often the first interaction a visitor has with your organization. A smooth, efficient check-in not only sets a positive tone but also enhances security by ensuring that you know who is entering your premises at all times. Traditional paper logbooks are increasingly being replaced by digital workplace solutions that offer a range of benefits.
What is a visitor management system?
A visitor management system is a digital solution designed to manage and track visitors entering a facility. It replaces manual methods like paper sign-in sheets with a more efficient and secure process. Here’s how a typical VMS works:
- Pre-registration: Visitors can pre-register their details before arriving, reducing wait times at the entrance.
- Self-service kiosks: Upon arrival, visitors use self-service kiosks to check in, scan identification, and print visitor badges.
- Integration with access control: The system can integrate with access control systems, granting visitors access to specific areas based on their role or purpose of visit.
- Real-time monitoring: Administrators can monitor visitor activity in real time and receive alerts for any unusual behavior or security threats.
The role of visitor management software
Visitor tracking software or visitor management software is another crucial component of a comprehensive visitor check-in solution. It provides detailed insights into visitor patterns, helping organizations make data-driven decisions. Here's why it's important:
- Real-time insights: Visitor tracking software offers real-time data on visitor movements and behaviors. This information can be used to optimize staffing levels, enhance security measures, and improve resource allocation.
- Historical data analysis: By analyzing historical data, organizations can identify trends and patterns in visitor behavior. This analysis can inform decisions about facility management, security protocols, and visitor experience improvements.
- Compliance and reporting: Visitor tracking software helps organizations comply with regulatory requirements by maintaining accurate visitor logs. It also simplifies the reporting process, making it easy to generate reports for audits or internal reviews.
Implementing a visitor management system
Implementing a visitor management system may seem like a complex task, but it can be broken down into manageable steps:
- Assess your needs: Identify the specific requirements of your organization and the features you need in a VMS.
- Research options: Explore different systems, focusing on those that meet your needs and offer the best integration capabilities.Streamline Visitor Check-In with a Modern Management System
- Pilot the system: Conduct a trial run to assess the system's effectiveness and gather feedback from staff and visitors.
- Train staff: Ensure that all relevant personnel are trained to use the system efficiently.
- Monitor and adjust: Continuously monitor the system's performance and make adjustments as needed to optimize its effectiveness.
Incorporating technology into your visitor check-in process is no longer a luxury—it's a necessity. A visitor management system, coupled with access control and visitor tracking software, offers a secure, efficient, and seamless experience for everyone involved.
By choosing the right visitor system and implementing it effectively, you can enhance security, improve data accuracy, and create a positive first impression for your visitors.
Are you ready to streamline your visitor check-in process?
Implementing a visitor management system can transform your organization’s check-in experience, enhancing both security and efficiency. If you're ready to take the next step, get in touch with us today to learn how Veris can help you create a seamless, secure visitor process.
Schedule a demo or talk to our workplace consultants for more information.
Jan 8, 2025
Read time: Loading...
Managing access control in large facilities with multiple buildings and restricted areas is no small task. As the complexity of workplaces grows, the need for effective multi-entry point access control systems has become essential. These systems ensure security, streamline operations, and provide administrators with the tools needed to manage resources efficiently.
This blog explores the challenges, best practices, and key features of multi-entry point access control systems, offering actionable insights for facility managers, administrators, and business owners.
Why multi-entry point access control is crucial
Managing access across several buildings and restricted zones presents unique challenges. Without an efficient system, administrators may struggle with:
- Inconsistent monitoring: Difficulty in tracking who enters and exits different areas in real time.
- Decentralized systems: Disconnected access control systems can lead to inefficiencies and security loopholes.
- Regulatory compliance risks: Sensitive areas require stringent controls to comply with data and security laws.
These challenges highlight why adopting a robust multi-entry point access control system is not just a convenience but a necessity for modern facilities.
Best practices for multi-entry point access control
1. Centralized dashboards for unified control
A centralized dashboard is a game-changer for managing multiple access points. It consolidates data from all entry points, providing real-time visibility and control.
How it helps:
- Administrators can monitor all activity from one platform.
- Access permissions can be modified instantly to meet dynamic needs.
2. Real-time monitoring for instant updates
Using IoT-enabled devices and cameras ensures real-time monitoring of all entry points. This feature not only enhances security but also allows for quick responses to potential breaches.
Benefits include:
- Immediate alerts for unauthorized access attempts.
- Proactive detection of suspicious activities, reducing risks.
3. Role-based access control (RBAC)
Role-based access ensures individuals can only access areas necessary for their responsibilities. It reduces internal risks and simplifies administrative workflows.
Use case example:
A manufacturing plant restricts access to its production floor to only authorized personnel, ensuring safety and compliance.
4. Integration with visitor management systems
Integrating visitor management systems with access control streamlines the onboarding process for guests. Pre-registration options and digital passes make the process seamless and secure.
Example feature:
Veris visitor management system integrates directly with access control, allowing administrators to grant and monitor guest access effortlessly.
Key features of multi-entry point access control systems

- Centralized dashboards: Manage multiple locations from one unified platform.
- Mobile accessibility: Admins can manage permissions and monitor activity using smartphones or tablets.
- Real-time alerts: Receive instant notifications for anomalies or breaches.
- Cloud integration: Secure and scalable storage of data with easy accessibility.
- Detailed reporting: Analyze access patterns to optimize resource allocation and identify inefficiencies.
Benefits of multi-entry point access control
- Enhanced security: Minimize unauthorized access with real-time monitoring and centralized control.
- Operational efficiency: Automate repetitive tasks like granting access and managing permissions, saving valuable time.

- Cost savings: Reduce dependence on manual security measures and invest in scalable solutions.
- Regulatory compliance: Ensure compliance with local and international security standards for sensitive areas.
Measuring success: metrics for multi-entry point access control
To evaluate the effectiveness of your access control system, track these key metrics:
- Unauthorized access attempts: Monitor and reduce incidents over time.
- Access log accuracy: Ensure all activity is logged correctly for compliance.
- System uptime: Track the reliability of your system to avoid downtime.
Take the first step toward enhanced security
A robust multi-entry point access control system is essential for ensuring security and efficiency in large facilities. By adopting the best practices outlined here, you can safeguard your resources, streamline operations, and foster a secure environment for employees and visitors alike.
Ready to enhance your facility’s security? Schedule a free demo with Veris today and explore our tailored solutions.
Jan 8, 2025
Read time: Loading...
In today’s fast-evolving work environment, organizations are rethinking how they engage with employees. Beyond salary and benefits, workplace experience has emerged as a key factor in employee satisfaction, productivity, and retention.
What is workplace experience?
Workplace experience is the sum of physical, emotional, and technological factors shaping how employees interact with their work environment. From the office layout to company culture and digital tools, every element plays a role in creating an environment where employees can thrive.
In this blog, we’ll explore the components of workplace experience, why it’s critical for modern organizations, how to measure it, and strategies to enhance it.
Key components of workplace experience
Workplace experience is shaped by how employees interact with their environment, which includes the physical workspace, digital tools, and overall workforce dynamics.
These elements must work cohesively to create a positive and engaging workplace experience, rather than one that feels merely adequate or, worse, counterproductive.
Take flexibility, for example—one of the most sought-after perks by employees today. The shift during and after the pandemic has elevated flexibility, such as hybrid or fully remote work, to a critical factor in job satisfaction. However, enabling flexible work options impacts all three components of workplace experience.
1. Physical environment
The layout and features of an office play a crucial role in influencing employees' comfort and productivity. Collaborative work thrives in open spaces, while quiet areas support concentration and focus. Flexible workspaces, including hot desks and collaborative zones, cater to the needs of hybrid workforces.
2. Workplace culture
Open spaces foster teamwork and interaction, while designated quiet zones enhance focus and productivity. A culture rooted in inclusivity, openness, and appreciation nurtures a supportive atmosphere where employees feel respected and inspired.
3. Technology and tools
Technology bridges the gap between convenience and productivity. Smart tools like visitor management systems, desk booking software, and meeting room solutions streamline workflows and reduce friction, allowing employees to focus on meaningful tasks.
Why workplace experience matters?
1. Boosts productivity
A well-designed workplace enables employees to work efficiently. Comfortable spaces, intuitive technology, and a supportive culture remove barriers to productivity.
2. Enhances talent retention
Employees are more likely to stay in an organization that prioritizes their well-being and experience. A positive workplace not only reduces turnover but also attracts top talent.
3. Strengthens brand reputation
Organizations with great workplace experiences are more likely to be recommended by employees, improving their reputation in the industry.
How to measure workplace experience
Measuring workplace experience is essential to understand what’s working and where improvements are needed. Here are some key metrics to track:

1. Employee feedback
Regular pulse surveys and satisfaction scores provide insights into how employees feel about the physical environment, tools, and culture.
2. Space utilization data
Track how desks, meeting rooms, and shared spaces are used to identify underutilized resources or overcrowded areas.
3. Employee retention rates
Monitor turnover rates to understand the impact of workplace improvements on employee loyalty.
4. Technology adoption rates
Analyze how frequently employees use workplace tools and systems to ensure they are meeting user needs.
Strategies to enhance workplace experience
- Optimize physical spaces: Redesign spaces to support both collaboration and focus. Flexible layouts, ergonomic furniture, and hybrid-friendly spaces go a long way in creating a productive environment.
- Foster a positive culture: Encourage open communication, recognize employee contributions, and organize activities that build connections across teams.
- Adopt smart technology: Leverage solutions like Veris visitor management system and desk booking to automate processes and provide seamless access to resources. These tools enhance not only operational efficiency but also employee satisfaction.
How Veris solutions elevate workplace experience?
Veris provides a range of solutions aimed at streamlining workplace processes and enhancing employee engagement:
- Visitor management system: Streamlines visitor check-ins with contactless processes and real-time notifications.
- Desk booking system: Enables employees to book workstations easily, supporting hybrid work models.
- Access control solutions: Ensures secure and hassle-free entry for employees and visitors.
By integrating these technologies, organizations can create an environment that is efficient, secure, and employee-centric.
Workplace experience is essential for creating a thriving organization. Whether it’s optimizing spaces, fostering a strong culture, or adopting smart tools, investing in workplace experience benefits both employees and the business.
Looking to elevate your workplace experience to new heights?
Schedule a free demo with Veris today and discover how our solutions can transform your workspace.
Jan 6, 2025
Read time: Loading...
In an era where efficiency and security are paramount, workplaces are evolving rapidly to meet modern challenges. Facial recognition systems (FR) are leading this transformation, offering seamless, contactless access control and advanced biometric authentication. These systems are not just a trend; they’re shaping the future of workplace security and management.
If you’re a facility manager, chief facility officer, or administrative leader, understanding the value of facial recognition technology is crucial. This blog delves into the problems it solves, how it works, its benefits, and why it’s a must-have for modern workplaces.
The problem with traditional access control systems
Workplaces still relying on traditional access control methods face several challenges:
- Security vulnerabilities: Access cards can be lost, stolen, or duplicated, creating risks of unauthorized entry.
- Operational inefficiencies: Manual processes like visitor check-ins and e badge issuance slow down workflows.
- Lack of real-time insights: Traditional systems fail to provide actionable data on space usage and visitor patterns.
- Hygiene concerns: Physical touchpoints in traditional systems pose health risks, especially in high-traffic areas.
These issues emphasize the importance of adopting a more reliable and streamlined solution.
What is a facial recognition system?
A facial recognition system is a biometric tool that recognizes or confirms a person's identity by examining their unique facial characteristics. It uses advanced algorithms to map key facial points and compare them against a database for authentication. This contactless, intuitive technology eliminates the need for physical IDs or passwords, making it ideal for workplaces, co-working spaces, and corporate offices.

Types of facial recognition systems and its uses
Facial recognition technology comes in various forms, each tailored to specific environments and use cases. From basic 2D imaging to advanced 3D mapping and thermal detection, these systems offer unique advantages for enhancing workplace security and efficiency. Here’s a closer look at the three main types and their applications.workplace securityw. Here’s a closer look at the three main types and their applications.

Why workplaces need facial recognition systems
- Enhanced security: Facial recognition eliminates risks associated with lost or stolen access cards, providing secure, biometric-based authentication.
- Contactless access: In high-traffic areas, minimizing physical touchpoints is crucial. Facial recognition offers a hygienic, hands-free solution.
- Operational efficiency: The system reduces delays by eliminating manual processes. Employees and visitors gain instant access with just a glance.
- Improved visitor management: Facial recognition streamlines visitor check-ins, enabling pre-registration and quick authentication upon arrival.
- Actionable insights: By integrating with workplace tools, facial recognition systems provide data on occupancy, peak usage times, and access patterns.
Major concerns around facial recognition system
- Privacy: Facial recognition systems adhere to strict data protection protocols, encrypting biometric data to prevent misuse.
- Integration challenges: Modern FR systems, like those offered by Veris, integrate seamlessly with existing workplace management tools, ensuring smooth adoption.
- Cost effectiveness: While the initial investment may seem significant, FR systems deliver long-term value through enhanced security and operational savings.
Future trends in facial recognition technology
The evolution of facial recognition is being shaped by emerging technologies:
- Integration with IoT: Advanced sensors and interconnected devices enable the seamless gathering of real-time data for improved insights.
- AI-powered analytics: Advanced AI improves accuracy and enables predictive insights.
- Multi-modal biometrics: Combining facial recognition with fingerprints or voice adds an extra layer of security.
These advancements ensure that facial recognition remains a future-ready solution for workplaces.
Key metrics track via facial recognition systems
When implementing facial recognition, organizations can track:
- Time saved during check-ins and access.
- Reduction in unauthorized access attempts.
- Occupancy patterns for resource optimization.
- Visitor and employee satisfaction levels.
Facial recognition systems are not just about improving security—they’re about transforming how workplaces operate. By adopting this cutting-edge technology, organizations can create safer, more efficient, and smarter environments.
Ready to upgrade your workplace?
Schedule a free demo or contact our experts to explore how Veris facial recognition solutions can help you achieve your security and efficiency goals.
Jan 3, 2025
Read time: Loading...
Managing real estate has always been complex, but today’s challenges are greater than ever. From optimizing spaces to tracking leases and ensuring sustainability, traditional methods fall short of meeting modern demands. Enter the integrated workplace management system (IWMS)—a powerful solution designed to transform real estate operations by streamlining processes and maximizing efficiency.
What is an integrated workplace management system (IWMS)?
An integrated workplace management system (IWMS) is a centralized platform that integrates various aspects of real estate management. It combines tools for space utilization, lease tracking, facility management, and more into one cohesive system. By providing real-time data and insights, IWMS empowers real estate teams to make informed decisions, reduce costs, and improve operational efficiency.
Challenges without integrated workplace management system
Real estate managers relying on outdated systems often face:

These challenges not only hinder productivity but also impact profitability.
How IWMS transforms real estate operations
1. Optimizing space utilization
IWMS delivers real-time insights into workspace utilization, enabling organizations to identify and optimize underused areas effectively. It supports hybrid work models by enabling flexible layouts, ensuring every square foot adds value.
2. Centralized lease and asset management
Say goodbye to missed lease renewals and penalties. IWMS tracks lease details and asset lifecycles in a single platform, ensuring proactive management and cost-saving.
3. Energy efficiency and sustainability
IWMS integrates energy monitoring tools, helping real estate teams track and reduce consumption. This approach reduces utility expenses while actively contributing to sustainability objectives.
4. Streamlined collaboration and decision-making
With all data accessible on a single platform, teams can collaborate effectively. Dashboards and automated reports provide insights that simplify strategic planning.
Benefits of integrated workplace management system (IWMS)
- Cost efficiency: By optimizing resource allocation and reducing manual tasks, IWMS lowers operational expenses.
- Enhanced productivity: Teams save time with automated workflows, allowing them to focus on high-priority tasks.
- Improved resource utilization: IWMS tracks desk and space usage, enabling reallocation of underused resources and reducing wastage.
- Regulatory compliance: IWMS ensures that all properties meet local safety and legal standards, mitigating risks.
- Scalability: From managing a single property to an expansive portfolio, IWMS adapts to the scale of operations effortlessly.
Real world example: Integrated workplace management system in action
Imagine a property management firm overseeing multiple office buildings. With IWMS:
- They track space utilization across locations in real-time.
- Lease renewals are automated, preventing penalties.
- Dashboards reveal underused spaces, enabling better allocation.
- This leads to reduced costs, improved operations, and happier tenants and employees.
Future Trends: Integrated workplace management system (IWMS)
IWMS is evolving rapidly, integrating with technologies like:

The future of real estate management is smart, connected, and data-driven.
Take the first step toward smarter real estate management
Efficient real estate operations start with the right tools. Veris integrated workplace management system (IWMS) empowers real estate managers to streamline processes, optimize resources, and reduce costs—all while supporting hybrid work models.
Ready to revolutionize your real estate management? Schedule a free demo today and discover how Veris IWMS can unlock your business’s potential.
Dec 30, 2024
Read time: Loading...
Workplace security isn’t just about physical safety—it’s about creating an environment where employees can thrive without concerns. Whether it’s protecting sensitive information, securing physical spaces, or ensuring seamless visitor management, adopting robust security measures is essential for modern workplaces. Here are 10 practical tips to strengthen your workplace security while fostering a safe and productive environment.
1. Implement a visitor management system
Gone are the days of manual sign-in sheets. A smart visitor management system (VMS), like Veris, streamlines visitor registration and ensures only authorized individuals enter your premises. Features like pre-registration, QR codes, and real-time notifications make the process seamless and secure.
2. Enforce role-based access control (RBAC)
Not every employee or visitor needs access to all areas. Implementing role-based access control ensures that access is granted only to those who need it. With Veris, you can manage access permissions dynamically, reducing the risk of unauthorized entry.
3. Monitor and track visitors in real-time
Tracking visitors in real-time is crucial for preventing security breaches. Veris VMS offers live dashboards, allowing administrators to monitor who’s on-site, their purpose, and their location within the premises.
4. Secure meeting and workspace areas
Unauthorized access to meeting rooms or restricted workspaces can pose serious risks. Veris meeting room booking system ensures that only approved personnel can reserve and access specific areas, providing an added layer of security.
5. Use digital credentials
Physical ID cards can be misplaced or duplicated. Instead, adopt digital credentials like QR codes or mobile passes for employees and visitors. Veris solutions provide secure digital access methods, minimizing risks associated with physical IDs.
6. Integrate security technology across systems
A fragmented security system can lead to blind spots. Veris integrates seamlessly with access control systems, surveillance cameras, and workplace management software to provide a holistic security approach.
7. Conduct regular security audits
Routine audits help identify vulnerabilities in your security protocols. Use insights from Veris dashboards to analyze visitor patterns, monitor access logs, and optimize your security measures.
8. Provide employees with security training
Educate employees on basic security practices, such as identifying phishing attempts, managing digital passwords, and reporting suspicious activity. A well-informed workforce is your first line of defense.
9. Plan for emergency scenarios
Whether it’s a fire drill or an active threat, having a clear emergency response plan is crucial. Veris solutions can assist in evacuation planning by providing real-time visitor and employee location data.
10. Prioritize data security
Workplace security isn’t just physical—it’s digital too. Ensure that sensitive employee and visitor data is encrypted and stored securely. Veris adheres to stringent compliance standards, ensuring your data remains protected.
Why Veris is your ideal workplace security partner
With Veris, workplace security goes beyond physical barriers. Our solutions combine cutting-edge technology with user-friendly interfaces, ensuring a safe, secure, and efficient workplace. From managing visitor access to securing workspaces and meeting rooms, Veris empowers you to stay ahead of potential risks.
Ready to enhance your workplace security?
Discover how Veris can transform your workplace into a secure and seamless environment. Schedule a free demo today!

Stay ahead of the curve with our handpicked selection of comprehensive and actionable resources like blogs, case studies, newsletters, podcasts, and guides, crafted to take you closer to industry excellence.













.avif)

.jpg)



.jpg)





.jpg)







.avif)
.avif)



